| Exam Name: | Certified Ethical Hacker Exam (CEHv12) | ||
| Exam Code: | 312-50v12 Dumps | ||
| Vendor: | ECCouncil | Certification: | CEH v12 |
| Questions: | 572 Q&A's | Shared By: | yuvraj |
Which mode of IPSec should you use to assure security and confidentiality of data within the same LAN?
Eve is spending her day scanning the library computers. She notices that Alice is using a computer whose port 445 is active and listening. Eve uses the ENUM tool to enumerate Alice machine. From the command prompt, she types the following command.
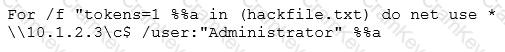
What is Eve trying to do?
An attacker, using a rogue wireless AP, performed an MITM attack and injected an HTML code to embed a malicious applet in all HTTP connections.
When users accessed any page, the applet ran and exploited many machines. Which one of the following tools the hacker probably used to inject HTML code?