CompTIA SecurityX Certification Exam
Last Update Mar 7, 2026
Total Questions : 619
To help you prepare for the CAS-004 CompTIA exam, we are offering free CAS-004 CompTIA exam questions. All you need to do is sign up, provide your details, and prepare with the free CAS-004 practice questions. Once you have done that, you will have access to the entire pool of CompTIA SecurityX Certification Exam CAS-004 test questions which will help you better prepare for the exam. Additionally, you can also find a range of CompTIA SecurityX Certification Exam resources online to help you better understand the topics covered on the exam, such as CompTIA SecurityX Certification Exam CAS-004 video tutorials, blogs, study guides, and more. Additionally, you can also practice with realistic CompTIA CAS-004 exam simulations and get feedback on your progress. Finally, you can also share your progress with friends and family and get encouragement and support from them.
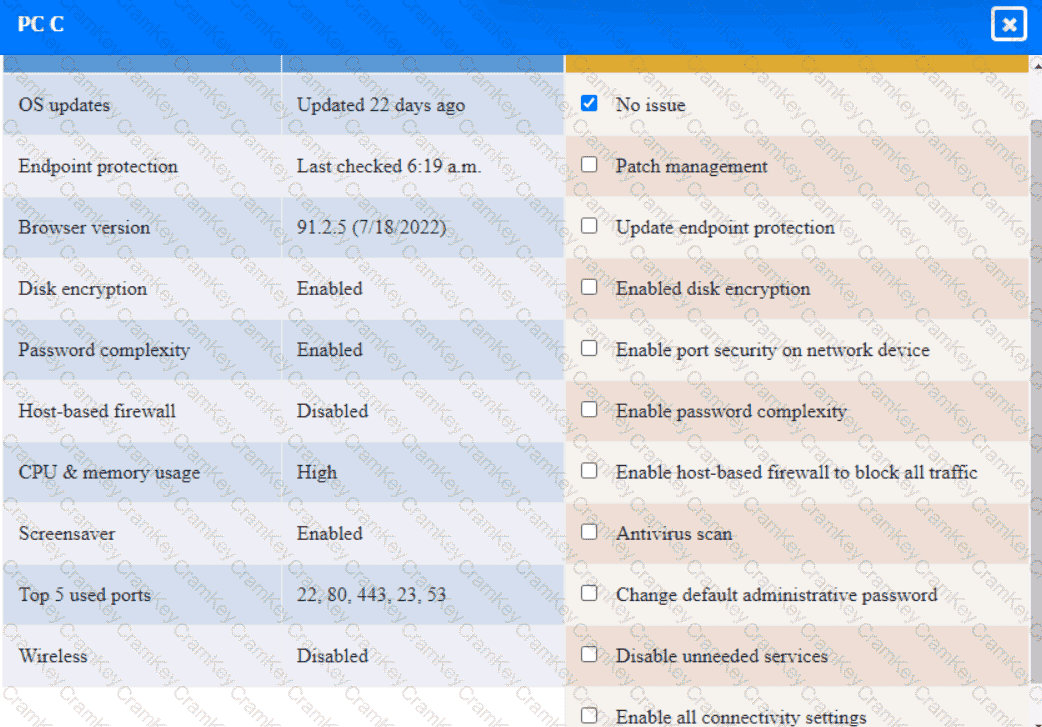
A security engineer needs to review the configurations of several devices on the network to meet the following requirements:
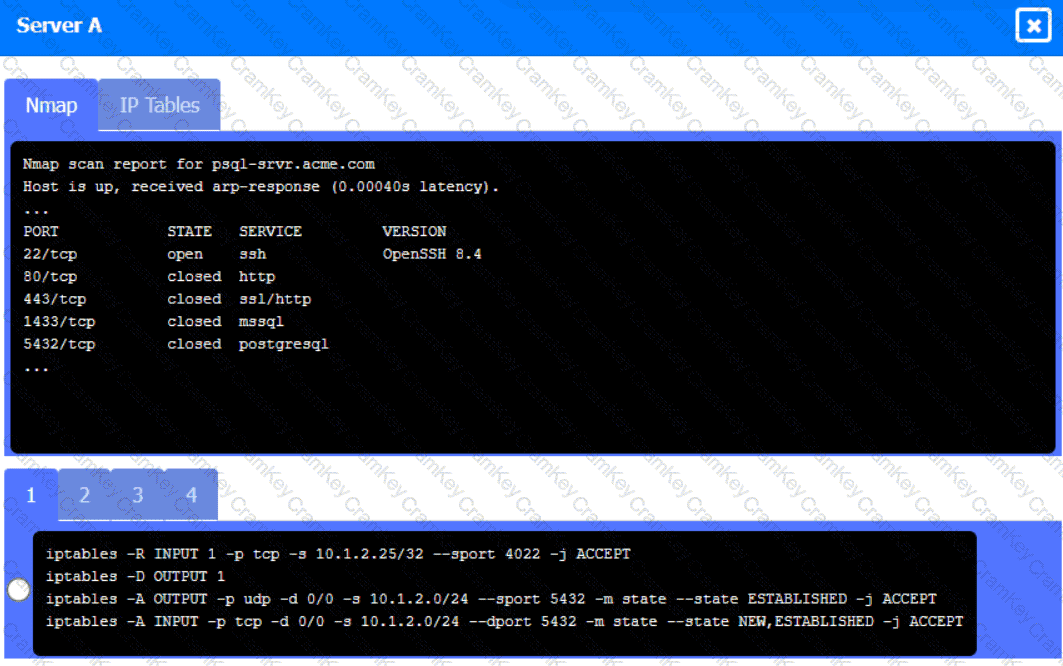
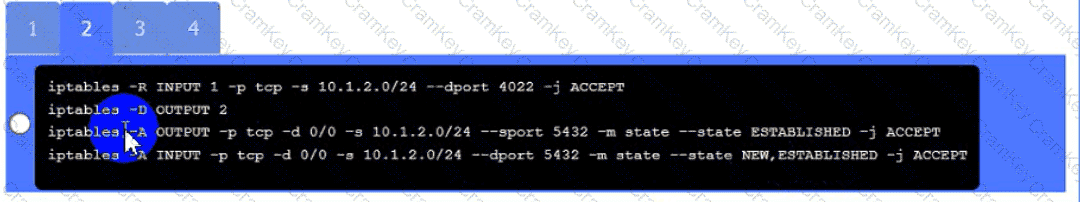
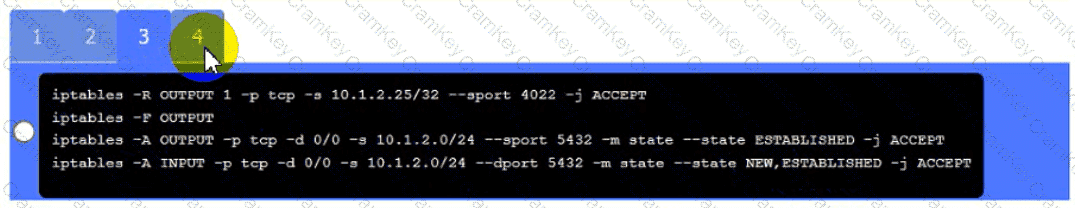
• The PostgreSQL server must only allow connectivity in the 10.1.2.0/24
subnet.
• The SSH daemon on the database server must be configured to listen
to port 4022.
• The SSH daemon must only accept connections from a Single
workstation.
• All host-based firewalls must be disabled on all workstations.
• All devices must have the latest updates from within the past eight
days.
• All HDDs must be configured to secure data at rest.
• Cleartext services are not allowed.
• All devices must be hardened when possible.
Instructions:
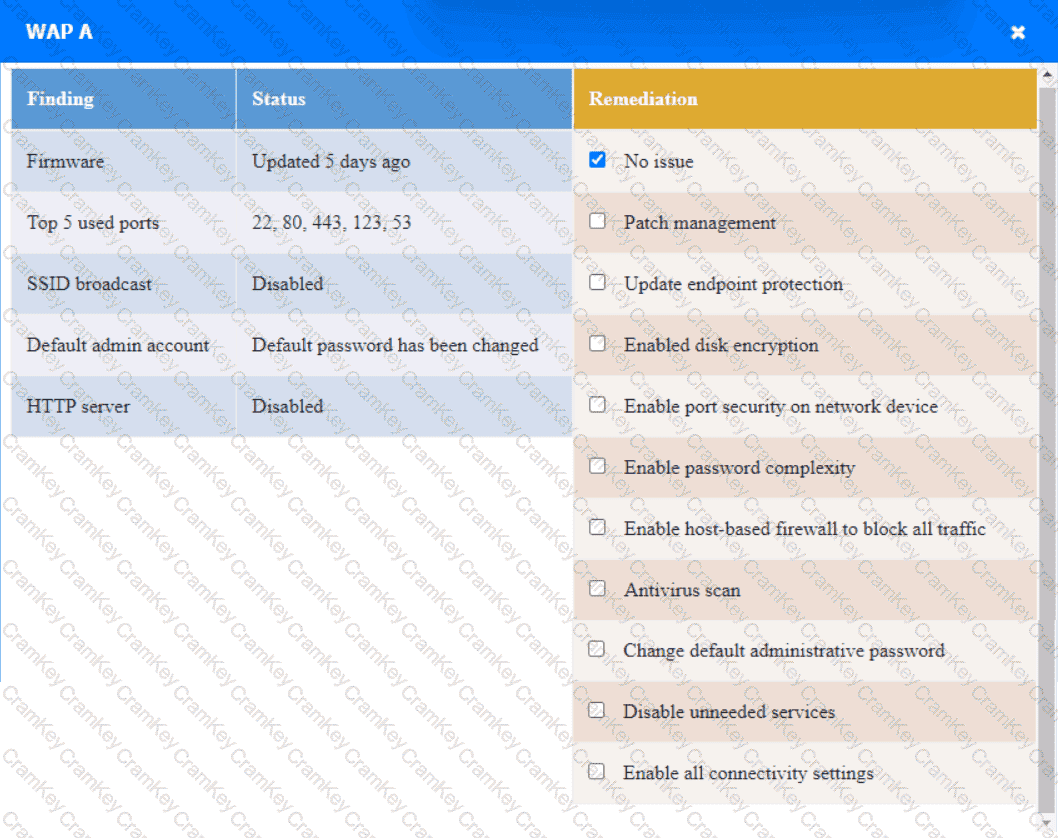
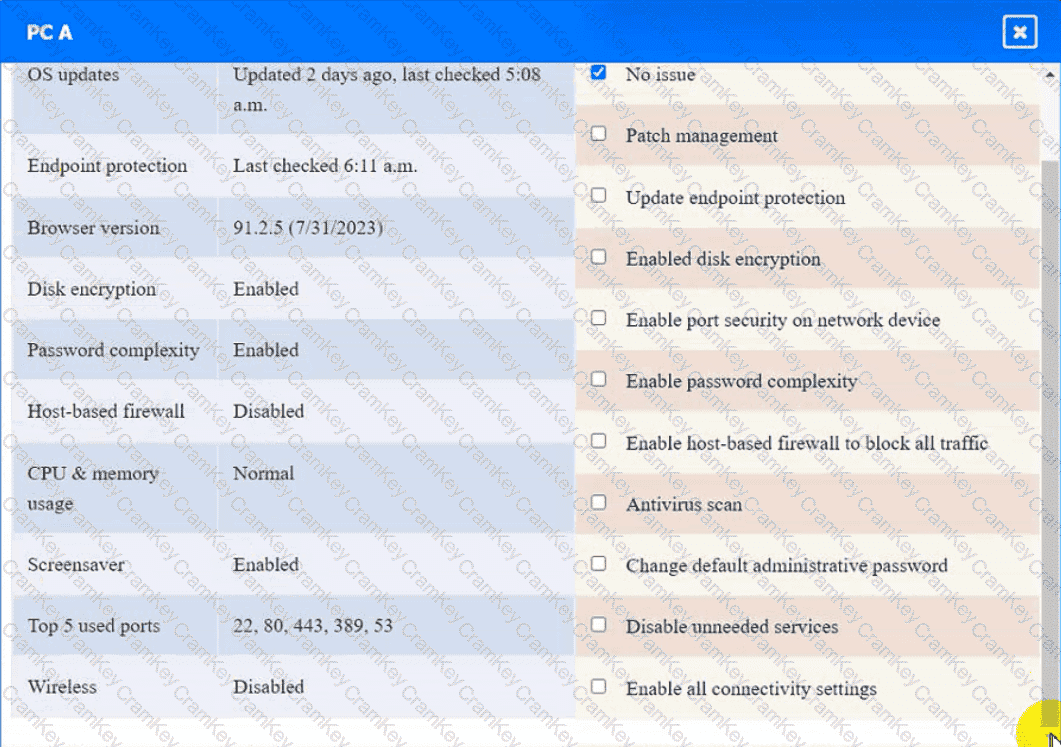
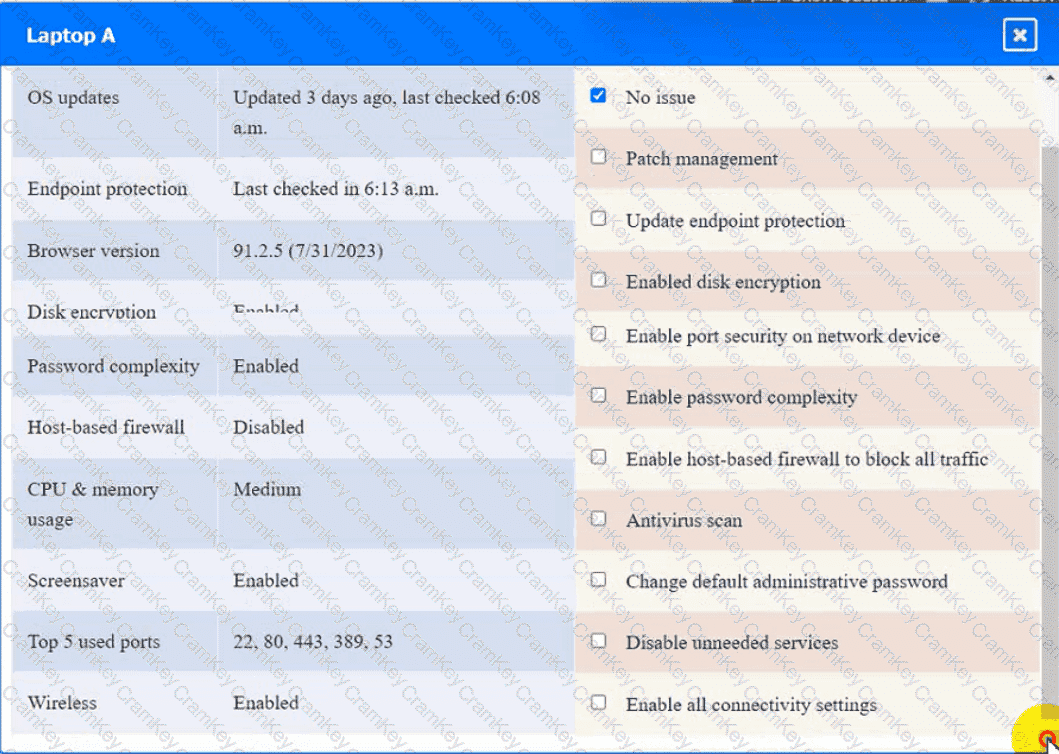
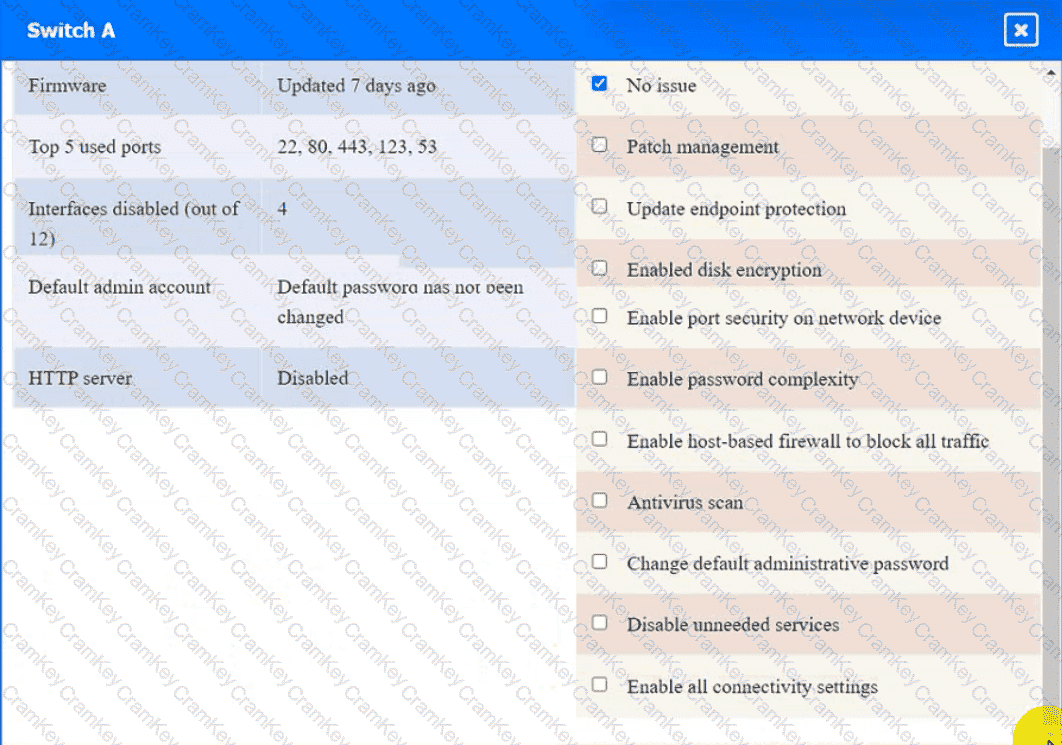
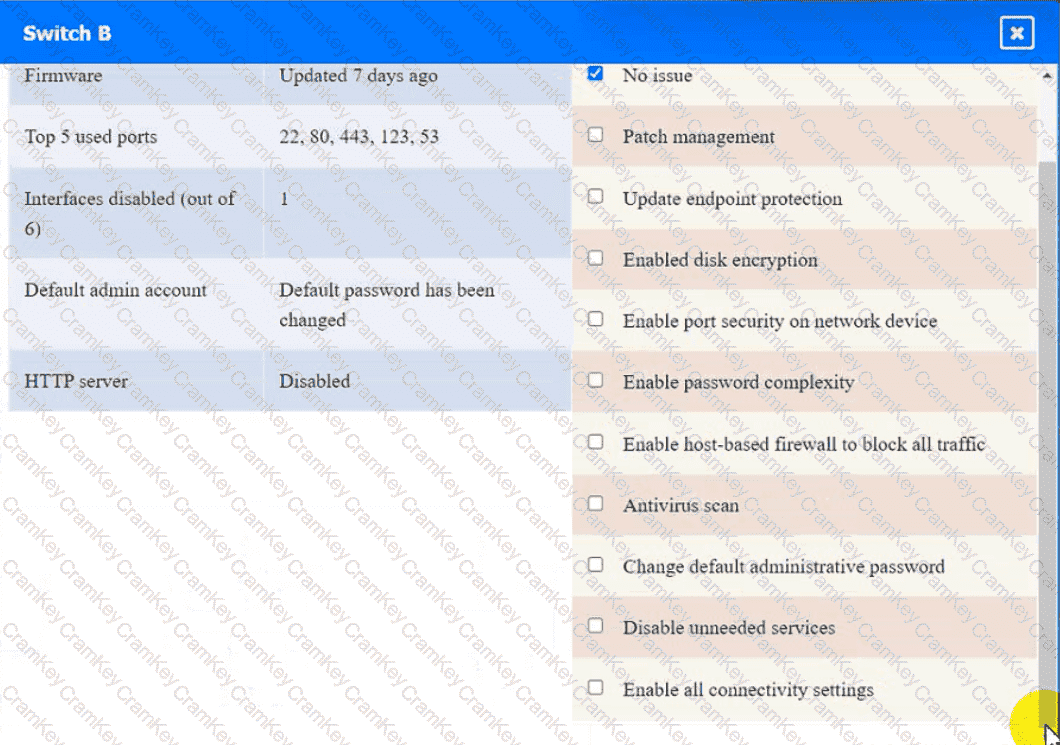
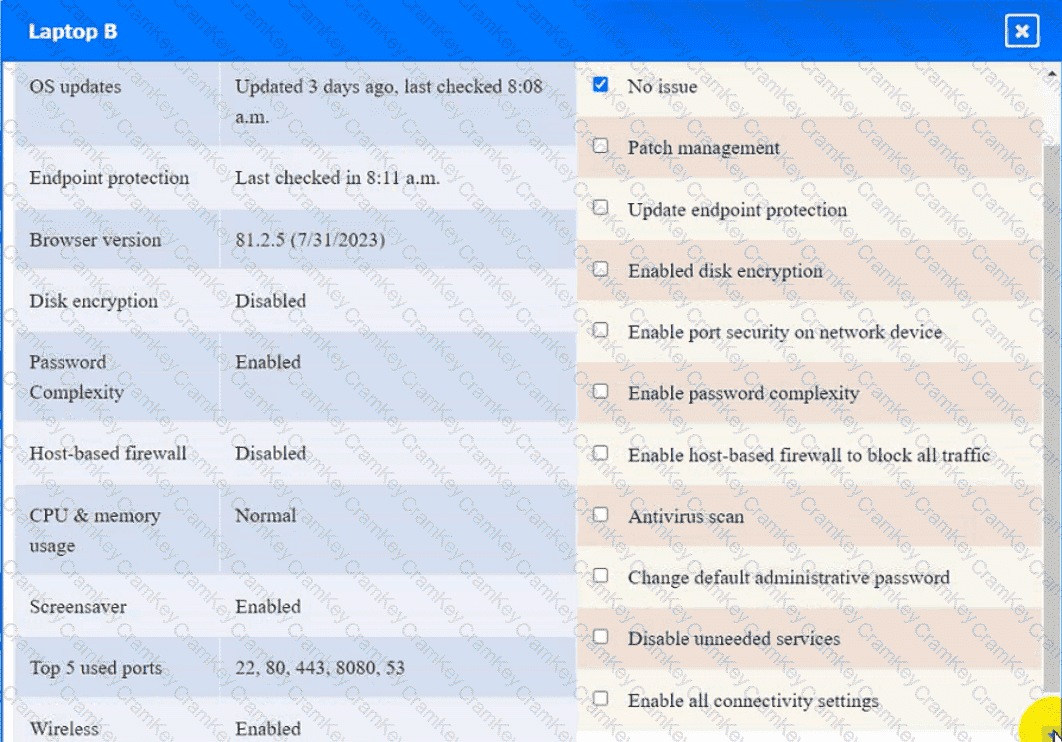
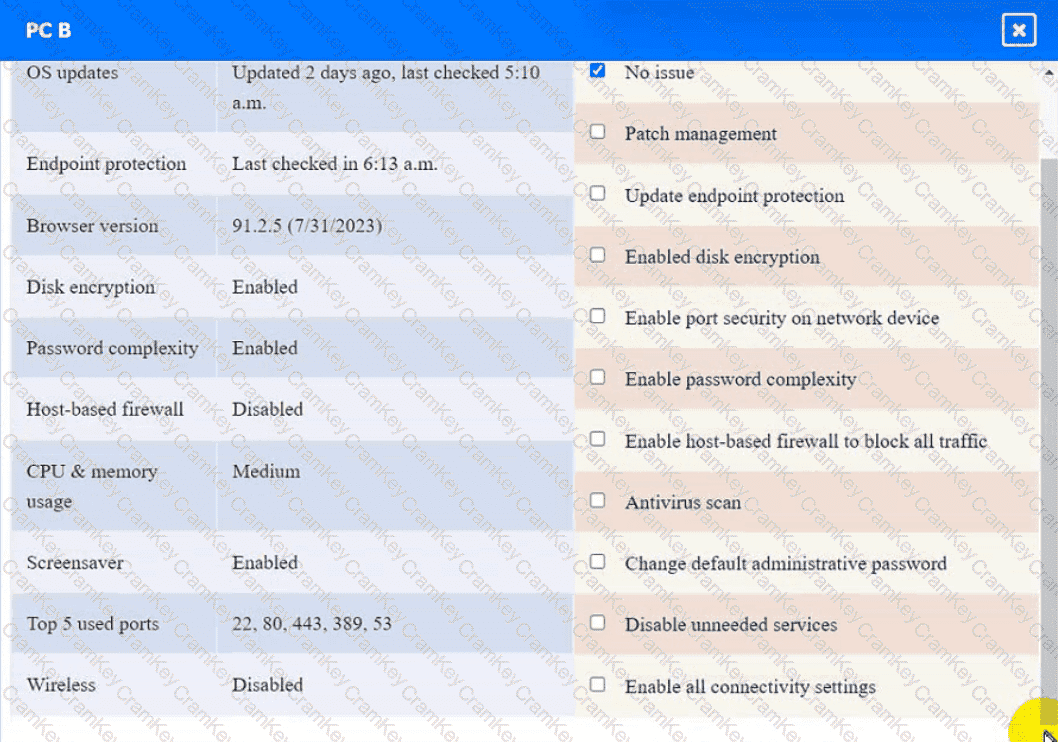
Click on the various workstations and network devices to review the posture assessment results. Remediate any possible issues or indicate that no issue is found.
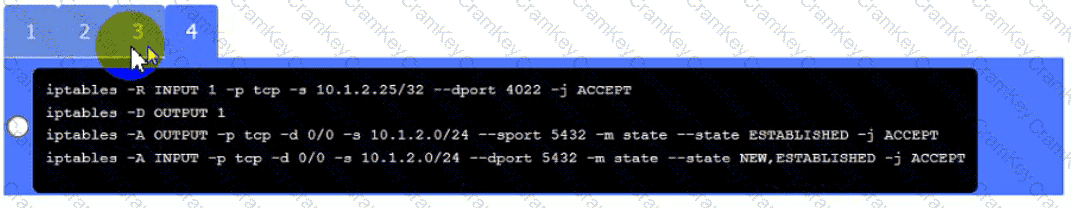
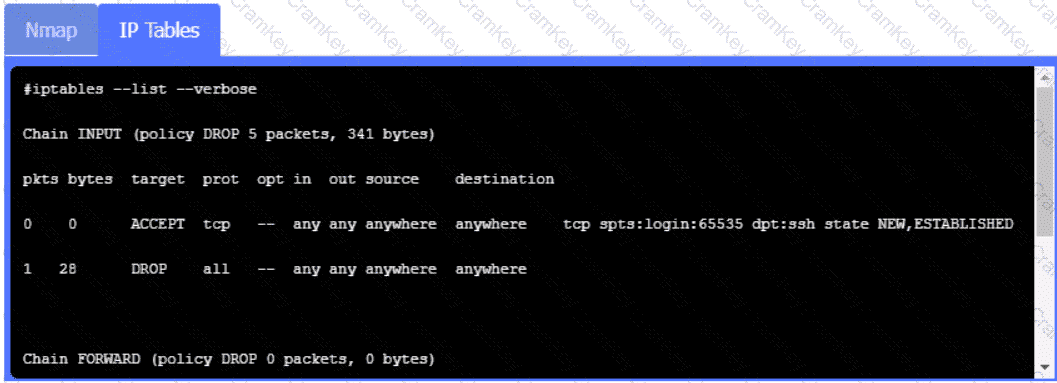
Click on Server A to review output data. Select commands in the appropriate tab to remediate connectivity problems to the pOSTGREsql DATABASE VIA ssh
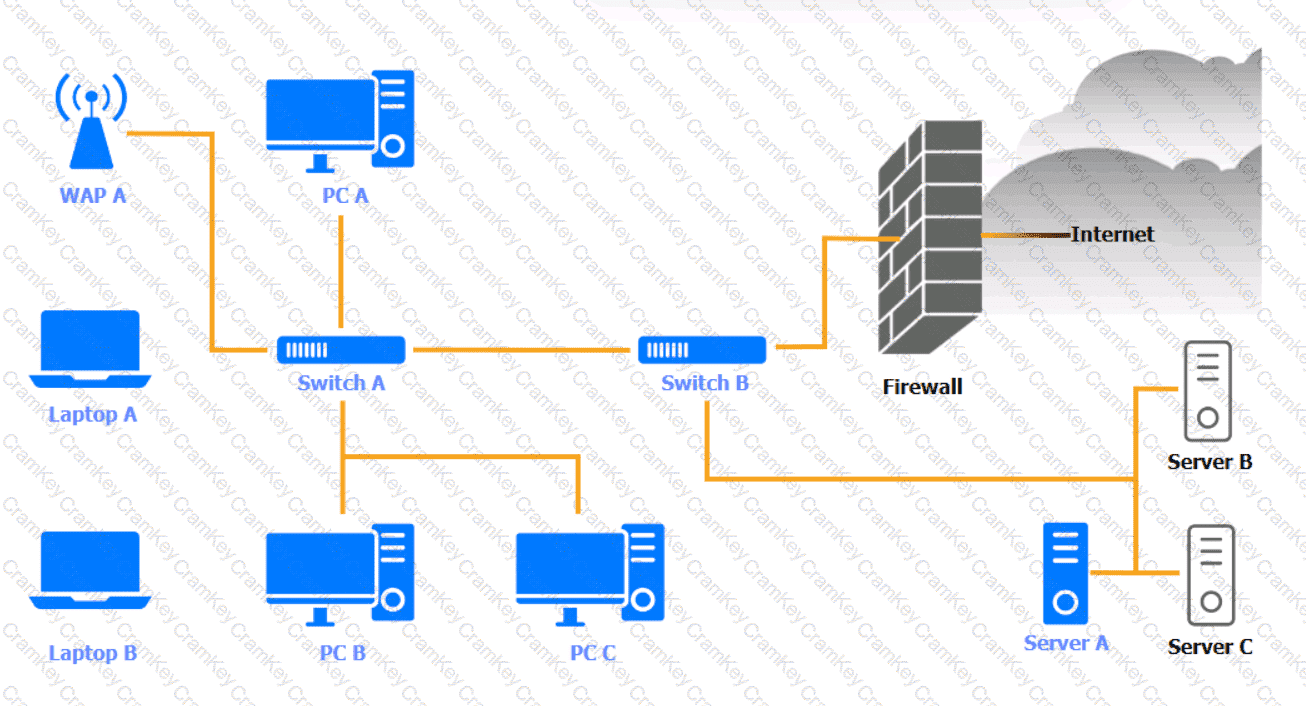
WAP A
PC A
Laptop A
Switch A
Switch B:
Laptop B
PC B
PC C
Server A
A company has decided that only administrators are permitted to use PowerShell on their Windows computers. Which of the following is the BEST way for an administrator to implement this decision?
A security administrator has been provided with three separate certificates and is trying to organize them into a single chain of trust to deploy on a website. Given the following certificate properties:
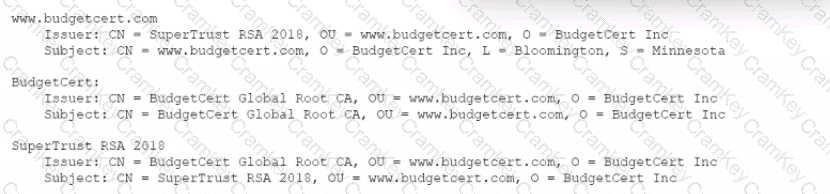
Which of the following are true about the PKI hierarchy? (Select two).
A network administrator for a completely air-gapped and closed system has noticed that anomalous external files have been uploaded to one of the critical servers. The administrator has reviewed logs
in the SIEM that were collected from security appliances, network infrastructure devices, and endpoints. Which of the following processes, if executed, would be MOST likely to expose an attacker?