| Exam Name: | Certified Ethical Hacker (CEH) | ||
| Exam Code: | CEH-001 Dumps | ||
| Vendor: | GAQM | Certification: | Certified Ethical Hacker CEH |
| Questions: | 878 Q&A's | Shared By: | nell |
In Trojan terminology, what is required to create the executable file chess.exe as shown below?
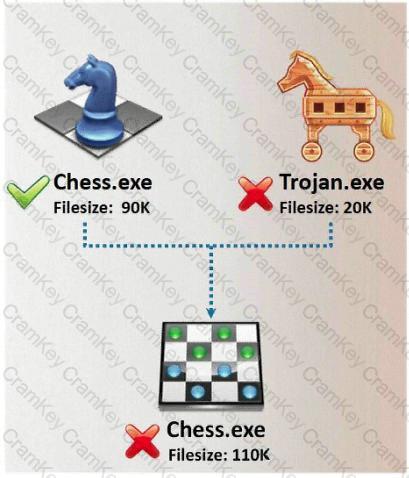
Joel and her team have been going through tons of garbage, recycled paper, and other rubbish in order to find some information about the target they are attempting to penetrate. How would you call this type of activity?
Google uses a unique cookie for each browser used by an individual user on a computer. This cookie contains information that allows Google to identify records about that user on its database. This cookie is submitted every time a user launches a Google search, visits a site using AdSense etc. The information stored in Google's database, identified by the cookie, includes
How would you prevent Google from storing your search keywords?
Vulnerability scanners are automated tools that are used to identify vulnerabilities and misconfigurations of hosts. They also provide information regarding mitigating discovered vulnerabilities.
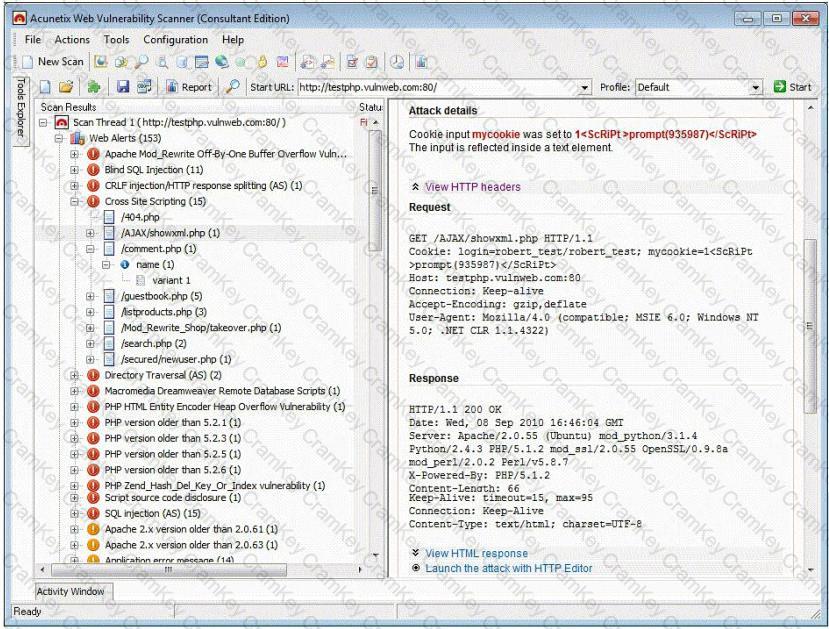
Which of the following statements is incorrect?