????Explanation:
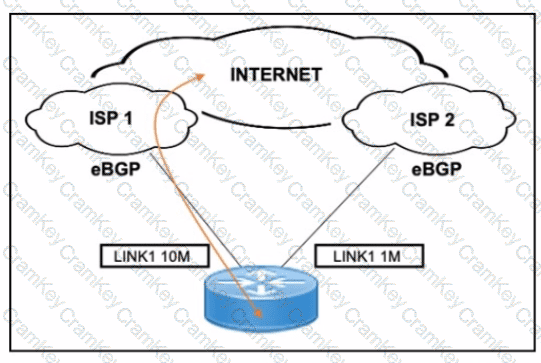
B: To prefer ISP 1 for outbound traffic, advertise a longer AS path to ISP 2 (so it's used as backup). To prefer ISP 1 for inbound traffic, you want ISP 2 to receive a higher MED, making it less preferred. These changes signal to both ISPs and remote ASes to prioritize the ISP 1 path.
Other options:
A: Local preference is set inbound by your own routers, not outbound to ISPs.
C: Local preference affects only your own AS, and more specific routes are better advertised on primary links, not secondary.
D: Advertising less specific routes does not help establish control over preference cleanly.
==========
???? QUESTION NO: 387 [Security, Automation, and Policy Integration in Design]
Which three components support enforcing security policy compliance for devices attempting network access? (Choose three)
A. Posture agent
B. Audit and decision point servers
C. Management and reporting tools
D. Endpoint security application
E. Network access devices
F. Web filtering devices
Answer: A, B, E
????Explanation:
A: Posture agents assess the health of endpoints (e.g., antivirus status, OS patching).
B: Decision servers (e.g., Cisco ISE) enforce access decisions based on posture and policies.
E: Network access devices (e.g., switches, WLCs, routers) apply access controls based on server instructions (802.1X, NAC).
Other options:
C: Management tools are for visibility—not enforcement.
D: While useful, endpoint AV/firewalls act independently—not part of policy enforcement infrastructure.
F: Web filters do not participate in initial access decisions.
==========
???? QUESTION NO: 388 [Security, Automation, and Policy Integration in Design]
When are Network Behavior Anomaly Detection (NBAD) systems better than signature-based systems? (Choose two)
A. Malware detection
B. Encrypted threat traffic
C. Spyware detection
D. Intrusion threat detection
E. New zero-day attacks
Answer: B, E
????Explanation:
B: Signature-based systems cannot inspect encrypted payloads effectively, whereas NBAD relies on traffic behavior.
E: NBAD identifies deviations from known good behavior, allowing detection of previously unknown (zero-day) threats.
Incorrect Options:
A, C, D: These are often more accurately detected using signature-based approaches where known
????QUESTION NO: 389
[Main Topic: Security, Automation, and Policy Integration in Design]
A company is adopting IPv6 in a dual-stack campus network. The first IPv6-only application is now hosted in the data center. To prevent a malicious user from masquerading as the IPv6 default gateway, which two mechanisms should be used? (Choose two)
A. IPv6 RA guard
B. IPv6 snooping
C. IPv6 device tracking
D. IPv6 address glean
E. port ACLs
Answer: A, E
????Comprehensive and Detailed Explanation (CCDE v3.1 aligned):
A. IPv6 RA Guard:This feature helps mitigate rogue router advertisements (RAs), which attackers can use to spoof the default gateway in an IPv6 environment. RA Guard drops unauthorized or unexpected RAs at the access layer switch ports, preventing malicious devices from advertising themselves as routers.
E. Port ACLs (PACLs):Port-based ACLs can restrict which devices are allowed to send or receive RA packets on switch ports. By tightly controlling which sources can send traffic (including RA messages), port ACLs help prevent spoofing attempts.
Other Options:
❌B. IPv6 Snooping:Not a standard or widely supported security feature; it is sometimes used synonymously with device tracking but is not a direct mitigation for spoofed RAs.
❌C. IPv6 Device Tracking:Useful for monitoring IP-to-MAC bindings, but it does not prevent spoofing or gateway impersonation.
❌D. IPv6 Address Glean:Primarily used for learning IPv6 addresses from traffic for things like DHCPv6 relay; not a security feature.
CCDE Blueprint Alignment:
Topic: Security, automation, and policy integration in design
Subdomain: IPv6 security, access control, rogue device prevention.
Let me know if you'd like the next question explained!