| Exam Name: | Cisco Certified Design Expert (CCDE v3.1) | ||
| Exam Code: | 400-007 Dumps | ||
| Vendor: | Cisco | Certification: | CCDE v3.0 |
| Questions: | 349 Q&A's | Shared By: | louise |
Which three components are part of the foundational information security principles of the CIA triad? (Choose three.)
Company XYZ network runs IPv4 and IPv6 and they want to introduce a multidomain, multicast-based network. The new design should use a flavor of PIM that forwards traffic using SPT. Which technology meets this requirement?
Which two actions ensure voice quality in a branch location with a low-speed, high-latency WAN connection? (Choose two.)
Refer to the exhibit.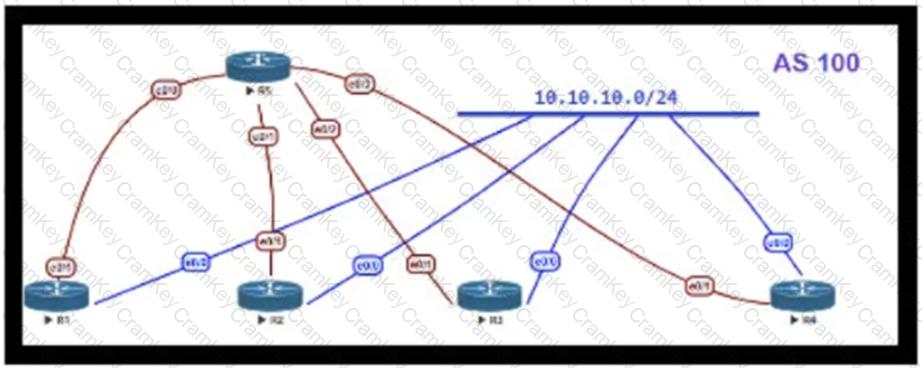
OSPF is running as the IGP to provide reachability to all AS100 networks. R3 and R4 are the current ABRs at the boundary of OSPF Area 0 and Area 1. Now BGP must be deployed within AS 100 because it will be receiving Internet routes from its eBGP peers (the service provider) connected to R1 and R2. What is an optimal solution for this deployment to configure BGP relationships and redistribute BGP learned routes into OSPF?