| Exam Name: | Ethical Hacking and Countermeasures V8 | ||
| Exam Code: | EC0-350 Dumps | ||
| Vendor: | ECCouncil | Certification: | Certified Ethical Hacker |
| Questions: | 878 Q&A's | Shared By: | alastair |
Jason is the network administrator of Spears Technology. He has enabled SNORT IDS to detect attacks going through his network. He receives Snort SMS alerts on his iPhone whenever there is an attempted intrusion to his network.
He receives the following SMS message during the weekend.
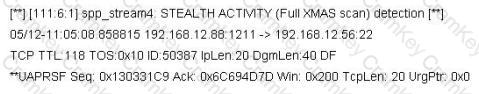
An attacker Chew Siew sitting in Beijing, China had just launched a remote scan on Jason's network with the hping command.
Which of the following hping2 command is responsible for the above snort alert?
File extensions provide information regarding the underlying server technology. Attackers can use this information to search vulnerabilities and launch attacks. How would you disable file extensions in Apache servers?
While testing web applications, you attempt to insert the following test script into the search area on the company's web site:
Later, when you press the search button, a pop up box appears on your screen with the text "Testing Testing Testing". What vulnerability is detected in the web application here?