CompTIA PenTest+ Certification Exam
Last Update Jan 28, 2026
Total Questions : 464
To help you prepare for the PT0-002 CompTIA exam, we are offering free PT0-002 CompTIA exam questions. All you need to do is sign up, provide your details, and prepare with the free PT0-002 practice questions. Once you have done that, you will have access to the entire pool of CompTIA PenTest+ Certification Exam PT0-002 test questions which will help you better prepare for the exam. Additionally, you can also find a range of CompTIA PenTest+ Certification Exam resources online to help you better understand the topics covered on the exam, such as CompTIA PenTest+ Certification Exam PT0-002 video tutorials, blogs, study guides, and more. Additionally, you can also practice with realistic CompTIA PT0-002 exam simulations and get feedback on your progress. Finally, you can also share your progress with friends and family and get encouragement and support from them.
Which of the following types of information would MOST likely be included in an application security assessment report addressed to developers? (Choose two.)
A penetration tester conducted a discovery scan that generated the following:
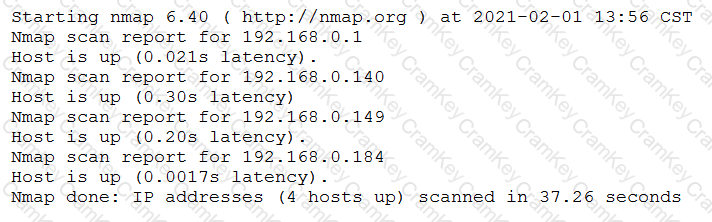
Which of the following commands generated the results above and will transform them into a list of active hosts for further analysis?
Which of the following types of information should be included when writing the remediation section of a penetration test report to be viewed by the systems administrator and technical staff?
A company is concerned that its cloud service provider is not adequately protecting the VMs housing its software development. The VMs are housed in a datacenter with other companies sharing physical resources. Which of the following attack types is MOST concerning to the company?