| Exam Name: | CompTIA PenTest+ Certification Exam | ||
| Exam Code: | PT0-002 Dumps | ||
| Vendor: | CompTIA | Certification: | PenTest+ |
| Questions: | 464 Q&A's | Shared By: | trent |
During an assessment, a penetration tester was able to access the organization's wireless network from outside of the building using a laptop running Aircrack-ng. Which of the following should be recommended to the client to remediate this issue?
A penetration tester gives the following command to a systems administrator to execute on one of the target servers:
rm -f /var/www/html/G679h32gYu.php
Which of the following BEST explains why the penetration tester wants this command executed?
A penetration tester downloaded a Java application file from a compromised web server and identifies how to invoke it by looking at the following log:
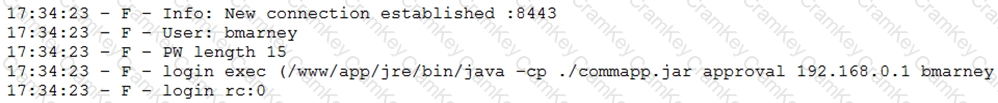
Which of the following is the order of steps the penetration tester needs to follow to validate whether the Java application uses encryption over sockets?
A security firm has been hired to perform an external penetration test against a company. The only information the firm received was the company name. Which of the following passive reconnaissance approaches would be MOST likely to yield positive initial results?