Computer Hacking Forensic Investigator (CHFI-v10)
Last Update Mar 10, 2026
Total Questions : 704
To help you prepare for the 312-49v10 ECCouncil exam, we are offering free 312-49v10 ECCouncil exam questions. All you need to do is sign up, provide your details, and prepare with the free 312-49v10 practice questions. Once you have done that, you will have access to the entire pool of Computer Hacking Forensic Investigator (CHFI-v10) 312-49v10 test questions which will help you better prepare for the exam. Additionally, you can also find a range of Computer Hacking Forensic Investigator (CHFI-v10) resources online to help you better understand the topics covered on the exam, such as Computer Hacking Forensic Investigator (CHFI-v10) 312-49v10 video tutorials, blogs, study guides, and more. Additionally, you can also practice with realistic ECCouncil 312-49v10 exam simulations and get feedback on your progress. Finally, you can also share your progress with friends and family and get encouragement and support from them.
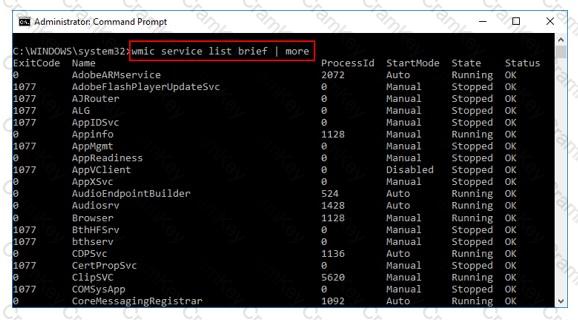
What is the investigator trying to view by issuing the command displayed in the following screenshot?
Which of the following network attacks refers to sending huge volumes of email to an address in an attempt to overflow the mailbox or overwhelm the server where the email address is hosted so as to cause a denial-of-service attack?
Michael works for Kimball Construction Company as senior security analyst. As part of yearly security audit, Michael scans his network for vulnerabilities. Using Nmap, Michael conducts XMAS scan and most of the ports scanned do not give a response. In what state are these ports?
You are running known exploits against your network to test for possible vulnerabilities. To test the strength of your virus software, you load a test network to mimic your production network. Your software successfully blocks some simple macro and encrypted viruses. You decide to really test the software by using virus code where the code rewrites itself entirely and the signatures change from child to child, but the functionality stays the same. What type of virus is this that you are testing?