| Exam Name: | Computer Hacking Forensic Investigator (CHFI-v10) | ||
| Exam Code: | 312-49v10 Dumps | ||
| Vendor: | ECCouncil | Certification: | CHFI v10 |
| Questions: | 704 Q&A's | Shared By: | herbie |
Which program uses different techniques to conceal a malware's code, thereby making it difficult for security mechanisms to detect or remove it?
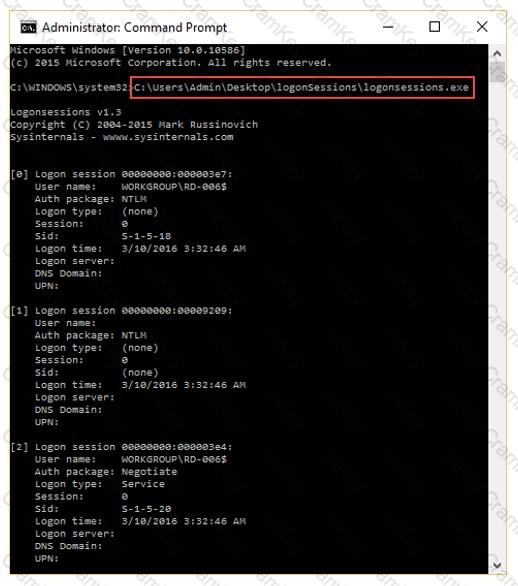
What is the investigator trying to analyze if the system gives the following image as output?
Which layer of iOS architecture should a forensics investigator evaluate to analyze services such as Threading, File Access, Preferences, Networking and high-level features?
Consider that you are investigating a machine running an Windows OS released prior to Windows Vista. You are trying to gather information about the deleted files by examining the master database file named INFO2 located at C:\Recycler\