| Exam Name: | Computer Hacking Forensic Investigator (CHFI-v10) | ||
| Exam Code: | 312-49v10 Dumps | ||
| Vendor: | ECCouncil | Certification: | CHFI v10 |
| Questions: | 704 Q&A's | Shared By: | philippa |
Chloe is a forensic examiner who is currently cracking hashed passwords for a crucial mission and hopefully solve the case. She is using a lookup table used for recovering a plain text password from cipher text; it contains word list and brute-force list along with their computed hash values. Chloe Is also using a graphical generator that supports SHA1.
a. What password technique is being used?
b. What tool is Chloe using?
Which of the following applications will allow a forensic investigator to track the user login sessions and user transactions that have occurred on an MS SQL Server?
You are the incident response manager at a regional bank. While performing routine auditing of web application logs, you find several attempted login submissions that contain the following strings:
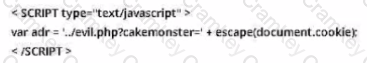
What kind of attack has occurred?
What happens lo the header of the file once It Is deleted from the Windows OS file systems?