| Exam Name: | Computer Hacking Forensic Investigator (CHFI-v10) | ||
| Exam Code: | 312-49v10 Dumps | ||
| Vendor: | ECCouncil | Certification: | CHFI v10 |
| Questions: | 704 Q&A's | Shared By: | baani |
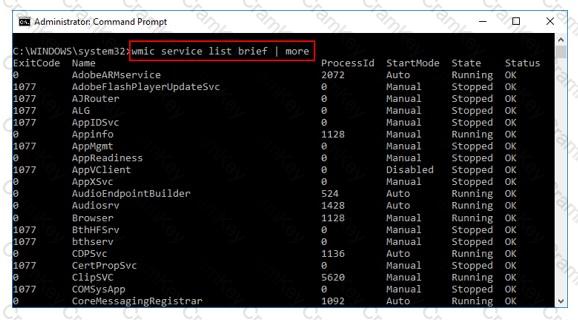
What is the investigator trying to view by issuing the command displayed in the following screenshot?
Which of the following standard represents a legal precedent set in 1993 by the Supreme Court of the United States regarding the admissibility of expert witnesses' testimony during federal legal proceedings?
In which of these attacks will a steganalyst use a random message to generate a stego-object by using some steganography tool, to find the steganography algorithm used to hide the information?
What is an investigator looking for in the rp.log file stored in a system running on Windows 10 operating system?