| Exam Name: | Computer Hacking Forensic Investigator (CHFI-v10) | ||
| Exam Code: | 312-49v10 Dumps | ||
| Vendor: | ECCouncil | Certification: | CHFI v10 |
| Questions: | 704 Q&A's | Shared By: | ariyan |
Sheila is a forensics trainee and is searching for hidden image files on a hard disk. She used a forensic investigation tool to view the media in hexadecimal code for simplifying the search process. Which of the following hex codes should she look for to identify image files?
The Apache server saves diagnostic information and error messages that it encounters while processing requests. The default path of this file is usr/local/apache/logs/error.log in Linux. Identify the Apache error log from the following logs.
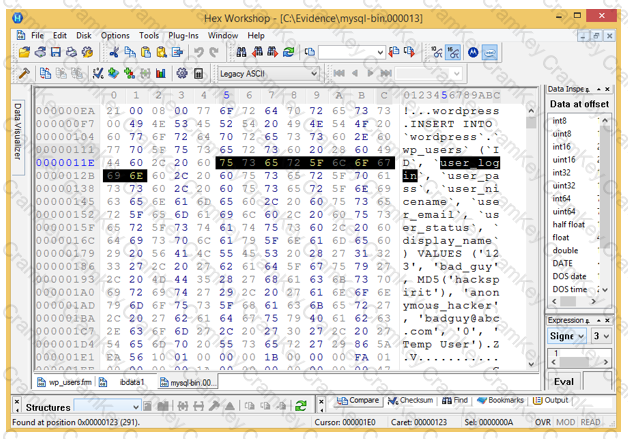
Analyze the hex representation of mysql-bin.000013 file in the screenshot below. Which of the following will be an inference from this analysis?