| Exam Name: | Certified Information Systems Security Professional (CISSP) | ||
| Exam Code: | CISSP Dumps | ||
| Vendor: | ISC | Certification: | ISC 2 Credentials |
| Questions: | 1486 Q&A's | Shared By: | elise |
Which of the following are required components for implementing software configuration management systems?
Refer to the information below to answer the question.
In a Multilevel Security (MLS) system, the following sensitivity labels are used in increasing levels of sensitivity: restricted, confidential, secret, top secret. Table A lists the clearance levels for four users, while Table B lists the security classes of four different files.
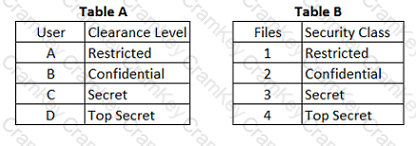
Which of the following is true according to the star property (*property)?
What do Capability Maturity Models (CMM) serve as a benchmark for in an organization?
Refer to the information below to answer the question.
A security practitioner detects client-based attacks on the organization’s network. A plan will be necessary to address these concerns.
What MUST the plan include in order to reduce client-side exploitation?