| Exam Name: | Certified Information Systems Security Professional (CISSP) | ||
| Exam Code: | CISSP Dumps | ||
| Vendor: | ISC | Certification: | ISC 2 Credentials |
| Questions: | 1486 Q&A's | Shared By: | nahla |
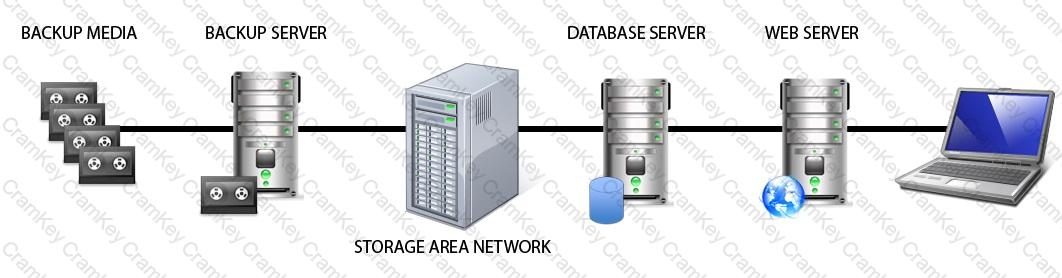
Identify the component that MOST likely lacks digital accountability related to information access.
Click on the correct device in the image below.
An organization publishes and periodically updates its employee policies in a file on their intranet. Which of the following is a PRIMARY security concern?
Which of the following is the MOST effective attack against cryptographic hardware modules?
Refer to the information below to answer the question.
An organization experiencing a negative financial impact is forced to reduce budgets and the number of Information Technology (IT) operations staff performing basic logical access security administration functions. Security processes have been tightly integrated into normal IT operations and are not separate and distinct roles.
Which of the following will be the PRIMARY security concern as staff is released from the organization?