Certified Ethical Hacker Exam
Last Update Mar 4, 2026
Total Questions : 614
To help you prepare for the 312-50 ECCouncil exam, we are offering free 312-50 ECCouncil exam questions. All you need to do is sign up, provide your details, and prepare with the free 312-50 practice questions. Once you have done that, you will have access to the entire pool of Certified Ethical Hacker Exam 312-50 test questions which will help you better prepare for the exam. Additionally, you can also find a range of Certified Ethical Hacker Exam resources online to help you better understand the topics covered on the exam, such as Certified Ethical Hacker Exam 312-50 video tutorials, blogs, study guides, and more. Additionally, you can also practice with realistic ECCouncil 312-50 exam simulations and get feedback on your progress. Finally, you can also share your progress with friends and family and get encouragement and support from them.
You receive an e-mail like the one shown below. When you click on the link contained in the mail, you are redirected to a website seeking you to download free Anti-Virus software.
Dear valued customers,
We are pleased to announce the newest version of Antivirus 2010 for Windows which will probe you with total security against the latest spyware, malware, viruses, Trojans and other online threats. Simply visit the link below and enter your antivirus code:
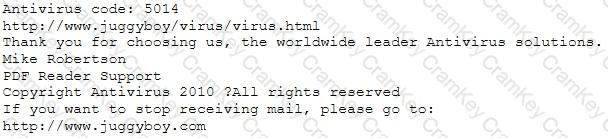
or you may contact us at the following address:
Media Internet Consultants, Edif. Neptuno, Planta
Baja, Ave. Ricardo J. Alfaro, Tumba Muerto, n/a Panama
How will you determine if this is Real Anti-Virus or Fake Anti-Virus website?
Jimmy is standing outside a secure entrance to a facility. He is pretending to have a tense conversation on his cell phone as an authorized employee badges in. Jimmy, while still on the phone, grabs the door as it begins to close.
What just happened?
Internet Protocol Security IPSec is actually a suite of protocols. Each protocol within the suite provides different functionality. Collective IPSec does everything except.