| Exam Name: | Certified Ethical Hacker Exam | ||
| Exam Code: | 312-50 Dumps | ||
| Vendor: | ECCouncil | Certification: | Certified Ethical Hacker |
| Questions: | 614 Q&A's | Shared By: | yasir |
Which of the following conditions must be given to allow a tester to exploit a Cross-Site Request Forgery (CSRF) vulnerable web application?
A company firewall engineer has configured a new DMZ to allow public systems to be located away from the internal network. The engineer has three security zones set:
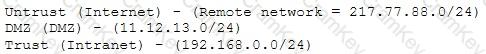
The engineer wants to configure remote desktop access from a fixed IP on the remote network to a remote desktop server in the DMZ. Which rule would best fit this requirement?
An attacker uses a communication channel within an operating system that is neither designed nor intended to transfer information. What is the name of the communications channel?