Securing Networks with Cisco Firepower (300-710 SNCF)
Last Update Mar 8, 2026
Total Questions : 385
To help you prepare for the 300-710 Cisco exam, we are offering free 300-710 Cisco exam questions. All you need to do is sign up, provide your details, and prepare with the free 300-710 practice questions. Once you have done that, you will have access to the entire pool of Securing Networks with Cisco Firepower (300-710 SNCF) 300-710 test questions which will help you better prepare for the exam. Additionally, you can also find a range of Securing Networks with Cisco Firepower (300-710 SNCF) resources online to help you better understand the topics covered on the exam, such as Securing Networks with Cisco Firepower (300-710 SNCF) 300-710 video tutorials, blogs, study guides, and more. Additionally, you can also practice with realistic Cisco 300-710 exam simulations and get feedback on your progress. Finally, you can also share your progress with friends and family and get encouragement and support from them.
A network administrator is trying to convert from LDAP to LDAPS for VPN user authentication on a Cisco FTD. Which action must be taken on the Cisco FTD objects to accomplish this task?
Within Cisco Firepower Management Center, where does a user add or modify widgets?
An engineer is setting up a new Firepower deployment and is looking at the default FMC policies to start the implementation During the initial trial phase, the organization wants to test some common Snort rules while still allowing the majority of network traffic to pass Which default policy should be used?
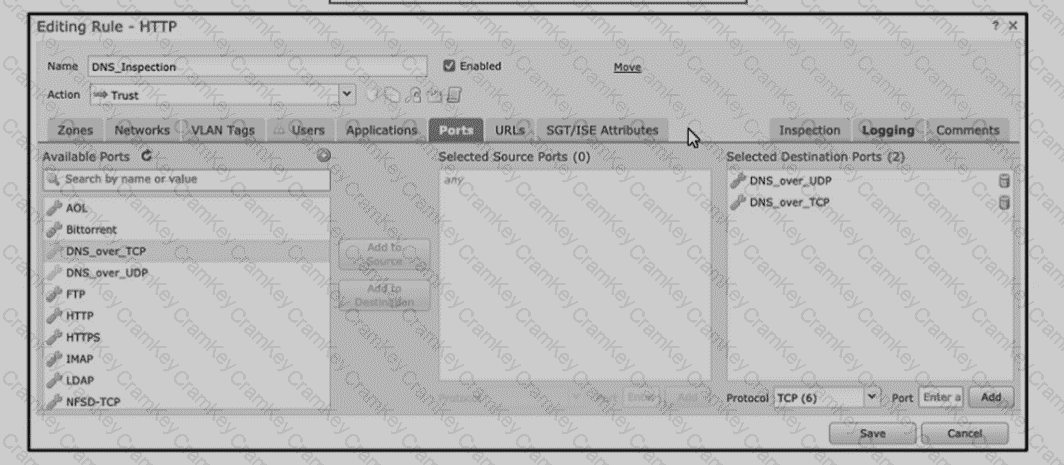
Refer to the exhibit An engineer is modifying an access control pokey to add a rule to inspect all DNS traffic that passes through the firewall After making the change and deploying thepokey they see that DNS traffic is not bang inspected by the Snort engine What is the problem?