| Exam Name: | PECB Certified ISO/IEC 27001 2022 Lead Auditor exam | ||
| Exam Code: | ISO-IEC-27001-Lead-Auditor Dumps | ||
| Vendor: | PECB | Certification: | ISO 27001 |
| Questions: | 418 Q&A's | Shared By: | lilia |
Question:
Which of the following statements regarding threats and vulnerabilities in information security is NOT correct?
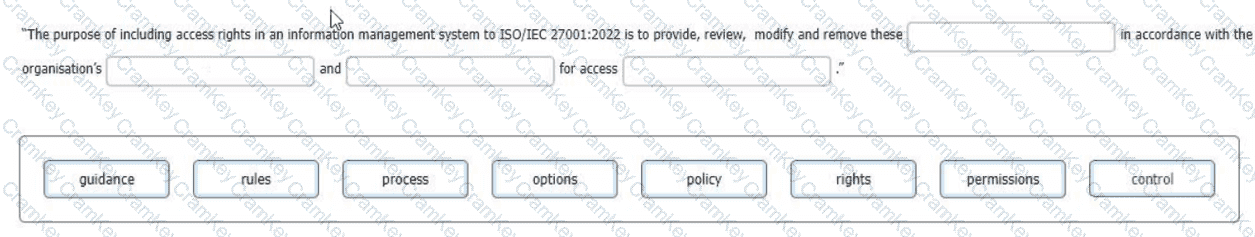
As the ISMS audit team leader, you are conducting a second-party audit of an international logistics company on behalf of an online retailer. During the audit, one of your team members reports a nonconformity relating to control 5.18 (Access rights) of Appendix A of ISO/IEC 27001:2022. She found evidence that removing the server access protocols of 20 people who left in the last 3 months took up to 1 week whereas the policy required removing access within 24 hours of their departure.
Complete the sentence with the best word(s), dick on the blank section you want to complete so that it is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop the option to the appropriate blank section.
Scenario 7
Lawsy is a leading law firm with offices in Bangkok, Thailand. It has over 50 attorneys offering sophisticated legal services to clients in business and commercial law, intellectual property, banking, and financial services. They believe they have a comfortable position in the market thanks to their commitment to implementing information security best practices and remaining up to date with technological developments.
Lawsy has rigorously implemented, evaluated, and conducted internal audits for the information security management system (ISMS) for two years. Now, they have applied for ISO/IEC 27001 certification at ISMA, a well-known and trusted certification body.
During the stage 1 audit, the audit team reviewed all the ISMS documents created during the implementation phase. They also reviewed and evaluated the records from management reviews and internal audits. Lawsy submitted records of evidence that corrective actions on nonconformities were performed when necessary, so the audit team interviewed the internal auditor. The interview validated the adequacy and frequency of the internal audits by providing insight into the internal audit plan and procedures.
The audit team continued verifying strategic documents, including the information security policy and risk evaluation criteria. During the information security policy review, the team noticed inconsistencies between the documented information describing the governance framework and the procedures. Following the completion of stage 1, the audit team leader prepared the audit plan, which addressed the audit objectives, scope, criteria, and procedures.
During the stage 2 audit, the audit team interviewed the information security manager, who drafted the information security policy. He justified the issue identified in stage 1 by stating that Lawsy conducts mandatory information security training and awareness sessions every three months.
Later, the audit team found that Lawsy did not have procedures for using laptops outside the workplace, even though employees were allowed to take laptops outside the workplace. The company only provided general information about the use of laptops and relied on employees’ common knowledge to protect the confidentiality and integrity of information stored on the laptops.
Following the interview, the audit team examined 15 employee training records (out of 50) and concluded that Lawsy meets the requirements of ISO/IEC 27001 related to training and awareness. To support this conclusion, the auditor photocopied and archived the examined employee training records after completing the audit.
Question
Lawsy lacks a procedure for using laptops outside the workplace and relies on employees' common knowledge to protect the confidentiality of information stored on the laptops. What does this present?