| Exam Name: | PECB Certified ISO/IEC 27001 2022 Lead Auditor exam | ||
| Exam Code: | ISO-IEC-27001-Lead-Auditor Dumps | ||
| Vendor: | PECB | Certification: | ISO 27001 |
| Questions: | 418 Q&A's | Shared By: | saif |
You are performing an ISMS audit at a residential nursing home called ABC that provides healthcare services.
The next step in your audit plan is to verify the information security on ABC's healthcare mobile app
development, support, and lifecycle process. During the audit, you learned the organization outsourced the
mobile app development to a professional software development company with CMMI Level 5, ITSM (ISO/IEC
20000-1), BCMS (ISO 22301) and ISMS (ISO/IEC 27001) certified. The IT Manager presented the software
security management procedure and summarised the process as follows:
The mobile app development shall adopt "security-by-design" and "security-by-default" principles, as a
minimum. The following security functions for personal data protection shall be available:
Access control.
Personal data encryption, i.e., Advanced Encryption Standard (AES) algorithm, key lengths: 256 bits; and
Personal data pseudonymization.
Vulnerability checked and no security backdoor
You sample the latest Mobile App Test report - details as follows:
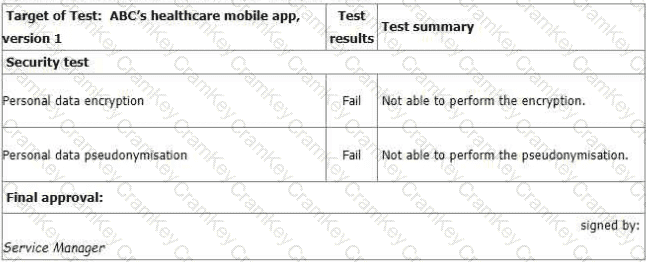
You ask the IT Manager why the organisation still uses the mobile app while personal data
encryption and pseudonymization tests failed. Also, whether the Service Manager is authorized to
approve the test.
The IT Manager explains the test results should be approved by him according to the software
security management procedure. The reason why the encryption and pseudonymization functions
failed is that these functions heavily slowed down the system and service performance. An extra
150% of resources are needed to cover this. The Service Manager agreed that access control is
good enough and acceptable. That's why the Service Manager signed the approval.
You sample one of the medical staff's mobile and found that ABC's healthcare mobile app, version
1.01 is installed. You found that version 1.01 has no test record.
The IT Manager explains that because of frequent ransomware attacks, the outsourced mobile app
development company gave a free minor update on the tested software, performed an emergency
release of the updated software, and gave a verbal guarantee that there will be no impact on any
security functions. Based on his 20 years of information security experience, there is no need to re-
test.
You are preparing the audit findings Select two options that are correct.
As an auditor, you have noticed that ABC Inc. has established a procedure to manage the removable storage media. The procedure is based on the classification scheme adopted by ABC Inc. Thus, if the information stored is classified as "confidential," the procedure applies. On the other hand, the information that is classified as "public," does not have confidentiality requirements: thus, only a procedure for ensuring its integrity and availability applies. What type of audit finding is this?
Scenario 7: Lawsy is a leading law firm with offices in New Jersey and New York City. It has over 50 attorneys offering sophisticated legal services to clients in business and commercial law, intellectual property, banking, and financial services. They believe they have a comfortable position in the market thanks to their commitment to implement information security best practices and remain up to date with technological developments.
Lawsy has implemented, evaluated, and conducted internal audits for an ISMS rigorously for two years now. Now, they have applied for ISO/IEC 27001 certification to ISMA, a well-known and trusted certification body.
During stage 1 audit, the audit team reviewed all the ISMS documents created during the implementation. They also reviewed and evaluated the records from management reviews and internal audits.
Lawsy submitted records of evidence that corrective actions on nonconformities were performed when necessary, so the audit team interviewed the internal auditor. The interview validated the adequacy and frequency of the internal audits by providing detailed insight into the internal audit plan and procedures.
The audit team continued with the verification of strategic documents, including the information security policy and risk evaluation criteria. During the information security policy review, the team noticed inconsistencies between the documented information describing governance framework (i.e., the information security policy) and the procedures.
Although the employees were allowed to take the laptops outside the workplace, Lawsy did not have procedures in place regarding the use of laptops in such cases. The policy only provided general information about the use of laptops. The company relied on employees' common knowledge to protect the confidentiality and integrity of information stored in the laptops. This issue was documented in the stage 1 audit report.
Upon completing stage 1 audit, the audit team leader prepared the audit plan, which addressed the audit objectives, scope, criteria, and procedures.
During stage 2 audit, the audit team interviewed the information security manager, who drafted the information security policy. He justified the Issue identified in stage 1 by stating that Lawsy conducts mandatory information security training and awareness sessions every three months.
Following the interview, the audit team examined 15 employee training records (out of 50) and concluded that Lawsy meets requirements of ISO/IEC 27001 related to training and awareness. To support this conclusion, they photocopied the examined employee training records.
Based on the scenario above, answer the following question:
Lawsy lacks a procedure regarding the use of laptops outside the workplace and it relies on employees' common knowledge to protect the confidentiality of information stored in the laptops. This presents:
Scenario 2
Knight is an electronics company based in Northern California, the US that develops video game consoles. With over 300 employees globally, Knight is celebrating its fifth anniversary by launching the G-Console, a next-generation gaming system aimed at international markets. G-Console is considered to be the ultimate media machine of 2021, and it will give players the best gaming experience. The console pack will include a pair of VR headsets, two games, and other gifts.
Over the years, the company has developed a strong reputation for integrity, honesty, and respect toward their customers. Besides being a very customer-oriented company, Knight also gained wide recognition within the gaming industry because of its quality.
As one of the leading video game console developers in the world, Knight often finds itself a target for malicious activities. Therefore, it has implemented an information security management system (ISMS) based on ISO/IEC 27001, and its scope was communicated to employees of the company over a weekly meeting.
Recently, however, Knight experienced a security breach when hackers leaked proprietary information. In response, the incident response team (IRT) immediately began a thorough investigation of the system and the specifics of the incident. Initially, the IRT suspected that employees may have used weak passwords, allowing hackers to easily access their accounts. Upon further investigation, it was revealed that the hackers captured traffic from the file transfer protocol (FTP), which transmits data using clear-text passwords for authentication.
In light of this security incident, and following the IRT’s recommendations, Knight decided to replace the FTP with Secure Shell (SSH) protocol. This change ensures that any captured traffic is encrypted, significantly improving security.
After implementing these changes, Knight conducted a risk assessment to verify that the implementation of controls had minimized the risk of similar incidents. Based on the results of the risk assessment, they chose a risk treatment option to treat the risk.
Question
According to Scenario 2, the ISMS scope was communicated to Knight’s employees at the weekly meeting. Is this acceptable?