| Exam Name: | PECB Certified ISO/IEC 27001 2022 Lead Auditor exam | ||
| Exam Code: | ISO-IEC-27001-Lead-Auditor Dumps | ||
| Vendor: | PECB | Certification: | ISO 27001 |
| Questions: | 418 Q&A's | Shared By: | lillian |
Scenario 6
Sinvestment is an insurance provider that offers a wide range of coverage options, including home, commercial, and life insurance. Originally established in North California, the company has expanded its operations to other locations, including Europe and Africa. In addition to its growth, Sinvestment is committed to complying with laws and regulations applicable to its industry and preventing any information security incident. They have implemented an information security management system (ISMS) based on ISO/IEC 27001 and have applied for certification.
A team of auditors was assigned by the certification body to conduct the audit. After signing a confidentiality agreement with Sinvestment, they started the audit activities. For the activities of the stage 1 audit, it was decided that they would be performed on site, except the review of documented information, which took place remotely, as requested by Sinvestment.
The audit team started the stage 1 audit by reviewing the documentation required, including the declaration of the ISMS scope, information security policies, and internal audit reports. The evaluation of the documented information was based on the content and procedure for managing the documented information.
In addition, the auditors found out that the documentation related to information security training and awareness programs was incomplete and lacked essential details. When asked, Sinvestment’s top management stated that the company has provided information security training sessions to all employees.
The stage 2 audit was conducted three weeks after the stage 1 audit. The audit team observed that the marketing department (not included in the audit scope) had no procedures to control employees’ access rights. Since controlling employees' access rights is one of the ISO/IEC 27001 requirements and was included in the company's information security policy, the issue was included in the audit report.
Question
Based on Scenario 6, when evaluating documented information, what action should the auditor have taken during the stage 1 audit?
Scenario 5: Cobt. an insurance company in London, offers various commercial, industrial, and life insurance solutions. In recent years, the number of Cobt's clients has increased enormously. Having a huge amount of data to process, the company decided that certifying against ISO/IEC 27001 would bring many benefits to securing information and show its commitment to continual improvement. While the company was well-versed in conducting regular risk assessments, implementing an ISMS brought major changes to its daily operations. During the risk assessment process, a risk was identified where significant defects occurred without being detected or prevented by the organizations internal control mechanisms.
The company followed a methodology to implement the ISMS and had an operational ISMS in place after only a few months After successfully implementing the ISMS, Cobt applied for ISO/IEC 27001 certification Sarah, an experienced auditor, was assigned to the audit Upon thoroughly analyzing the audit offer, Sarah accepted her responsibilities as an audit team leader and immediately started to obtain general information about Cobt She established the audit criteria and objective, planned the audit, and assigned the audit team members' responsibilities.
Sarah acknowledged that although Cobt has expanded significantly by offering diverse commercial and insurance solutions, it still relies on some manual processes Therefore, her initial focus was to gather information on how the company manages its information security risks Sarah contacted Cobt's representatives to request access to information related to risk management for the off-site review, as initially agreed upon for part of the audit However, Cobt later refused, claiming that such information is too sensitive to be accessed outside of the company This refusal raised concerns about the audit's feasibility, particularly regarding the availability and cooperation of the auditee and access to evidence Moreover, Cobt raised concerns about the audit schedule, stating that it does not properly reflect the recent changes the company made It pointed out that the actions to be performed during the audit apply only to the initial scope and do not encompass the latest changes made in the audit scope
Sarah also evaluated the materiality of the situation, considering the significance of the information denied for the audit objectives. In this case, the refusal by Cobt raised questions about the completeness of the audit and its ability to provide reasonable assurance. Following these situations, Sarah decided to withdraw from the audit before a certification agreement was signed and communicated her decision to Cobt and the certification body. This decision was made to ensure adherence to audit principles and maintain transparency, highlighting her commitment to consistently upholding these principles.
Based on the scenario above, answer the following question:
Question:
What type of risk did Cobt identify during the last risk assessment?
Scenario 9: Techmanic is a Belgian company founded in 1995 and currently operating in Brussels. It provides IT consultancy, software design, and hardware/software services, including deployment and maintenance. The company serves sectors like public services, finance, telecom, energy, healthcare, and education. As a customer-centered company, it prioritizes strong client relationships and leading security practices.
Techmanic has been ISO/IEC 27001 certified for a year and regards this certification with pride. During the certification audit, the auditor found some inconsistencies in its ISMS implementation. Since the observed situations did not affect the capability of its ISMS to achieve the intended results, Techmanic was certified after auditors followed up on the root cause analysis and corrective actions remotely During that year, the company added hosting to its list of services and requested to expand its certification scope to include that area The auditor in charge approved the request and notified Techmanic that the extension audit would be conducted during the surveillance audit
Techmanic underwent a surveillance audit to verify its iSMS's continued effectiveness and compliance with ISO/IEC 27001. The surveillance audit aimed to ensure that Techmanic’s security practices, including the recent addition of hosting services, aligned seamlessly with the rigorous requirements of the certification
The auditor strategically utilized the findings from previous surveillance audit reports in the recertification activity with the purpose of replacing the need for additional recertification audits, specifically in the IT consultancy sector. Recognizing the value of continual improvement and learning from past assessments. Techmanic implemented a practice of reviewing previous surveillance audit reports. This proactive approach not only facilitated identifying and resolving potential nonconformities but also aimed to streamline the recertification process in the IT consultancy sector.
During the surveillance audit, several nonconformities were found. The ISMS continued to fulfill the ISO/IEC 27001*s requirements, but Techmanic failed to resolve the nonconformities related to the hosting services, as reported by its internal auditor. In addition, the internal audit report had several inconsistencies, which questioned the independence of the internal auditor during the audit of hosting services. Based on this, the extension certification was not granted. As a result. Techmanic requested a transfer to another certification body. In the meantime, the company released a statement to its clients stating that the ISO/IEC 27001 certification covers the IT services, as well as the hosting services.
Based on the scenario above, answer the following question:
Question:
Auditors recommended Techmanic for certification after following up on corrective actions remotely. Is this acceptable?
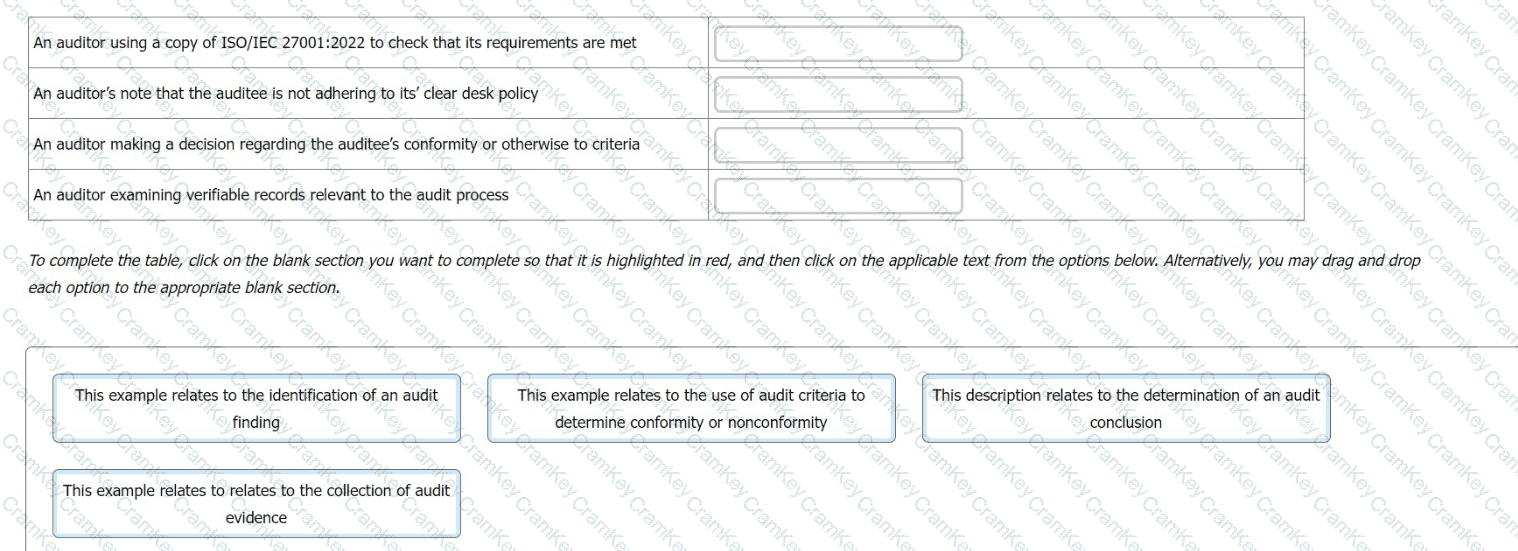
You are an experienced ISMS audit team leader, assisting an auditor in training to write their first audit report.
You want to check the auditor in training's understanding of terminology relating to the contents of an audit report and chose to do this by presenting the following examples.
For each example, you ask the auditor in training what the correct term is that describes the activity
Match the activity to the description.