| Exam Name: | PECB Certified ISO/IEC 27001 2022 Lead Auditor exam | ||
| Exam Code: | ISO-IEC-27001-Lead-Auditor Dumps | ||
| Vendor: | PECB | Certification: | ISO 27001 |
| Questions: | 418 Q&A's | Shared By: | rufus |
You are performing an ISMS initial certification audit at a residential nursing home that provides healthcare services. The next step in your audit plan is to conduct the closing meeting. During the final audit team meeting, as an audit team leader, you agree to report 2 minor nonconformities and 1 opportunity for improvement as below:
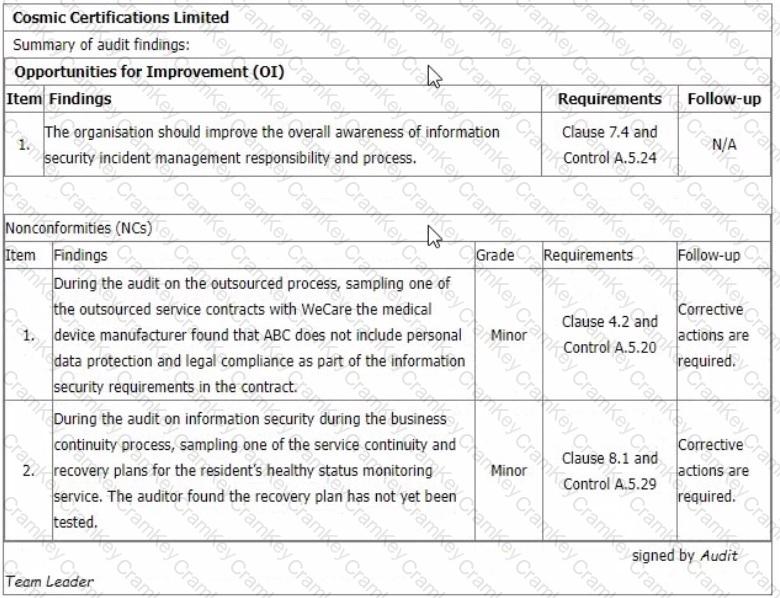
Select one option of the recommendation to the audit programme manager you are going to advise to the auditee at the closing meeting.
Scenario 4
SendPay is a financial services company specializing in global money transfers through a network of agents and institutions. As a new company in the market, SendPay aims to deliver top-quality services with its fee-free digital platform, launched last year, enabling clients to send and receive money anytime via smartphones and laptops. At that time, SendPay outsourced software operations to an external team, which also managed the company's technology infrastructure.
Recently, the company applied for ISO/IEC 27001 certification after having an ISMS in place for almost a year.
During the audit, the auditors focused on reviewing SendPay’s outsourced operations, specifically looking at the software development and technology infrastructure maintenance handled by the outsourced company. They followed a structured approach, which included reviewing and evaluating SendPay’s processes for monitoring the quality of these outsourced operations. This included verifying if the company met its contractual obligations, ensuring proper governance procedures for engaging outsourced entities, and assessing SendPay’s plans in case of expected or unexpected termination of outsourcing agreements.
However, the auditors subtly noted that SendPay’s protocols did not fully address contingencies for unanticipated cancellations of outsourcing agreements. Additionally, a technical expert appointed by SendPay assisted the auditors, providing specific knowledge and expertise related to the outsourced operations being audited.
The audit team calculated the number of training hours employees received on ISMS to ensure alignment with established objectives. They also computed the average resolution time of information security incidents based on a sample taken during the audit, which provided valuable insights into SendPay’s incident management practices. In addition, the auditors evaluated the reliability of the evidence collected during the audit. They considered several factors influencing the reliability of audit evidence. For example, evidence from surveillance cameras provided more objective proof compared to photos. Timing also played a crucial role in reliability, with mechanisms like transaction recording enhancing the credibility of the evidence.
SendPay uses cloud-based platforms to make its operations more efficient and scalable. However, during the audit, the auditors did not request SendPay to provide an inventory of their cloud activities due to resource limitations, relying instead on SendPay’s representations.
Question
Did the auditors establish a thorough understanding of SendPay’s cloud environment during the audit process? Refer to Scenario 4.
Scenario 7: Webvue. headquartered in Japan, is a technology company specializing in the development, support, and maintenance of computer software. Webvue provides solutions across various technology fields and business sectors. Its flagship service is CloudWebvue, a comprehensive cloud computing platform offering storage, networking, and virtual computing services. Designed for both businesses and individual users. CloudWebvue is known for its flexibility, scalability, and reliability.
Webvue has decided to only include CloudWebvue in its ISO/IEC 27001 certification scope. Thus, the stage 1 and 2 audits were performed simultaneously Webvue takes pride in its strictness regarding asset confidentiality They protect the information stored in CloudWebvue by using appropriate cryptographic controls. Every piece of information of any classification level, whether for internal use. restricted, or confidential, is first encrypted with a unique corresponding hash and then stored in the cloud
The audit team comprised five persons Keith. Sean. Layla, Sam. and Tina. Keith, the most experienced auditor on the IT and information security auditing team, was the audit team leader. His responsibilities included planning the audit and managing the audit team. Sean and Layla were experienced in project planning, business analysis, and IT systems (hardware and application) Their tasks included audit planning according to Webvue’s internal systems and processes Sam and Tina, on the other hand, who had recently completed their education, were responsible for completing the day-to-day tasks while developing their audit skills
While verifying conformity to control 8.24 Use of cryptography of ISO/IEC 27001 Annex A through interviews with the relevant staff, the audit team found out that the cryptographic keys have been initially generated based on random bit generator (RBG) and other best practices for the generation of the cryptographic keys. After checking Webvue's cryptography policy, they concluded that the information obtained by the interviews was true. However, the cryptographic keys are still in use because the policy does not address the use and lifetime of cryptographic keys.
As later agreed upon between Webvue and the certification body, the audit team opted to conduct a virtual audit specifically focused on verifying conformity to control 8.11 Data Masking of ISO/IEC 27001 within Webvue, aligning with the certification scope and audit objectives. They examined the processes involved in protecting data within CloudWebvue. focusing on how the company adhered to its policies and regulatory standards. As part of this process. Keith, the audit team leader, took screenshot copies of relevant documents and cryptographic key management procedures to document and analyze the effectiveness of Webvue's practices.
Webvue uses generated test data for testing purposes. However, as determined by both the interview with the manager of the QA Department and the procedures used by this department, sometimes live system data are used. In such scenarios, large amounts of data are generated while producing more accurate results. The test data is protected and controlled, as verified by the simulation of the encryption process performed by Webvue's personnel during the audit
While interviewing the manager of the QA Department, Keith observed that employees in the Security Training Department were not following proper procedures, even though this department fell outside the audit scope. Despite the exclusion in the audit scope, the non conformity in the Security Training Department has potential implications for the processes within the audit scope, specifically impacting data security and cryptographic practices in CloudWebvue. Therefore, Keith incorporated this finding into the audit report and accordingly informed the auditee.
Based on the scenario above, answer the following question:
Question:
Based on Scenario 7, the audit team checked Webvue’s cryptography policy to obtain reasonable assurance of the information obtained during interviews. Which type of audit procedure has been used?
Scenario 9: UpNet, a networking company, has been certified against ISO/IEC 27001. It provides network security, virtualization, cloud computing, network hardware, network management software, and networking technologies.
The company's recognition has increased drastically since gaining ISO/IEC 27001 certification. The certification confirmed the maturity of UpNefs operations and its compliance with a widely recognized and accepted standard.
But not everything ended after the certification. UpNet continually reviewed and enhanced its security controls and the overall effectiveness and efficiency of the ISMS by conducting internal audits. The top management was not willing to employ a full-time team of internal auditors, so they decided to outsource the internal audit function. This form of internal audits ensured independence, objectivity, and that they had an advisory role about the continual improvement of the ISMS.
Not long after the initial certification audit, the company created a new department specialized in data and storage products. They offered routers and switches optimized for data centers and software-based networking devices, such as network virtualization and network security appliances. This caused changes to the operations of the other departments already covered in the ISMS certification scope.
Therefore. UpNet initiated a risk assessment process and an internal audit. Following the internal audit result, the company confirmed the effectiveness and efficiency of the existing and new processes and controls.
The top management decided to include the new department in the certification scope since it complies with ISO/IEC 27001 requirements. UpNet announced that it is ISO/IEC 27001 certified and the certification scope encompasses the whole company.
One year after the initial certification audit, the certification body conducted another audit of UpNefs ISMS. This audit aimed to determine the UpNefs ISMS fulfillment of specified ISO/IEC 27001 requirements and ensure that the ISMS is being continually improved. The audit team confirmed that the certified ISMS continues to fulfill
the requirements of the standard. Nonetheless, the new department caused a significant impact on governing the management system. Moreover, the certification body was not informed about any changes. Thus, the UpNefs certification was suspended.
Based on the scenario above, answer the following question:
UpNet outsourced the internal audit function, as provided in scenario 9. Does it impact the internal audit process?