| Exam Name: | Certified Ethical Hacker Exam (CEH v11) | ||
| Exam Code: | 312-50v11 Dumps | ||
| Vendor: | ECCouncil | Certification: | CEH v11 |
| Questions: | 528 Q&A's | Shared By: | izaan |
If a token and 4-digit personal identification number (PIN) are used to access a computer system and the token performs off-line checking for the correct PIN, what type of attack is possible?
Which of the following statements is FALSE with respect to Intrusion Detection Systems?
ViruXine.W32 virus hides their presence by changing the underlying executable code.
This Virus code mutates while keeping the original algorithm intact, the code changes itself each time it runs, but the function of the code (its semantics) will not change at all.
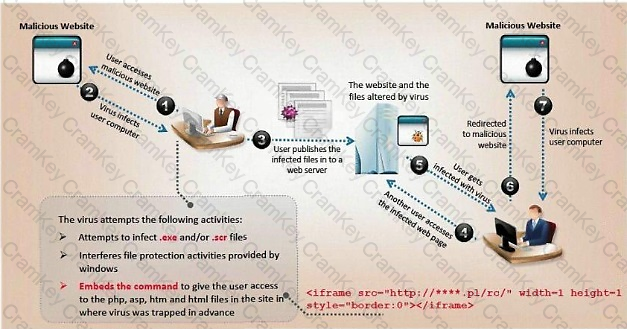
Here is a section of the Virus code:
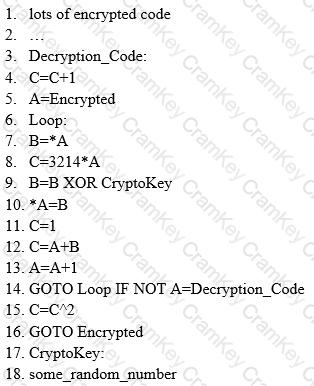
What is this technique called?