| Exam Name: | Certified Ethical Hacker Exam (CEH v11) | ||
| Exam Code: | 312-50v11 Dumps | ||
| Vendor: | ECCouncil | Certification: | CEH v11 |
| Questions: | 528 Q&A's | Shared By: | zayyan |
Clark, a professional hacker, was hired by an organization lo gather sensitive Information about its competitors surreptitiously. Clark gathers the server IP address of the target organization using Whole footprinting. Further, he entered the server IP address as an input to an online tool to retrieve information such as the network range of the target organization and to identify the network topology and operating system used in the network. What is the online tool employed by Clark in the above scenario?
Which tier in the N-tier application architecture is responsible for moving and processing data between the tiers?
Which among the following is the best example of the hacking concept called "clearing tracks"?
An attacker runs netcat tool to transfer a secret file between two hosts.
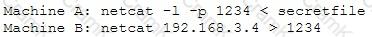
He is worried about information being sniffed on the network.
How would the attacker use netcat to encrypt the information before transmitting onto the wire?