| Exam Name: | Certified Ethical Hacker Exam (CEH v11) | ||
| Exam Code: | 312-50v11 Dumps | ||
| Vendor: | ECCouncil | Certification: | CEH v11 |
| Questions: | 528 Q&A's | Shared By: | alayah |
You are programming a buffer overflow exploit and you want to create a NOP sled of 200 bytes in the program exploit.c
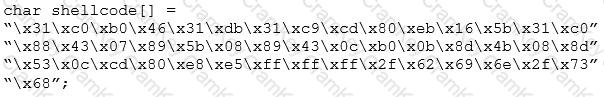
What is the hexadecimal value of NOP instruction?