| Exam Name: | CompTIA Security+ Exam 2025 | ||
| Exam Code: | SY0-701 Dumps | ||
| Vendor: | CompTIA | Certification: | CompTIA Security+ |
| Questions: | 762 Q&A's | Shared By: | alfie-james |
Which of the following digital forensics activities would a security team perform when responding to legal requests in a pending investigation?
An organization recently updated its security policy to include the following statement:
Regular expressions are included in source code to remove special characters such as $, |, ;. &, `, and ? from variables set by forms in a web application.
Which of the following best explains the security technique the organization adopted by making this addition to the policy?
The executive management team is mandating the company develop a disaster recovery plan. The cost must be kept to a minimum, and the money to fund additional internet connections is not available. Which of the following would be the best option?
A security administrator recently reset local passwords and the following values were recorded in the system:
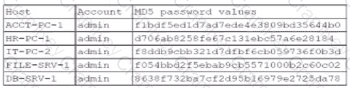
Which of the following in the security administrator most likely protecting against?