| Exam Name: | Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) | ||
| Exam Code: | 200-201 Dumps | ||
| Vendor: | Cisco | Certification: | CyberOps Associate |
| Questions: | 476 Q&A's | Shared By: | isa |
What is the impact of false positive alerts on business compared to true positive?
Which type of attack occurs when an attacker is successful in eavesdropping on a conversation between two IP phones?
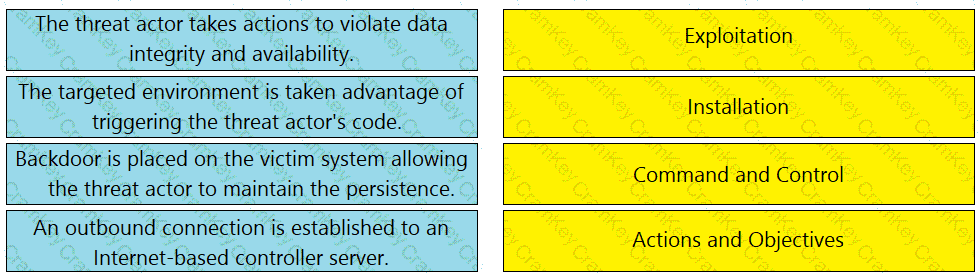
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
A vulnerability analyst is performing the monthly scan data review Output data is very big and getting bigger each month The analyst decides to create a more efficient process to complete the task on time All false positives and true positives are excluded from the results The remaining findings will be assigned to a technical team for further remediation What is the result of such activity?