| Exam Name: | Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) | ||
| Exam Code: | 200-201 Dumps | ||
| Vendor: | Cisco | Certification: | CyberOps Associate |
| Questions: | 476 Q&A's | Shared By: | amalia |
An investigator is examining a copy of an ISO file that is stored in CDFS format. What type of evidence is this file?
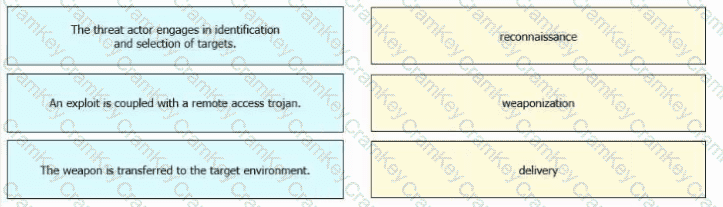
Drag and drop the definitions from the left onto the phases on the right to classify intrusion events according to the Cyber Kill Chain model.
What is a difference between signature-based and behavior-based detection?