| Exam Name: | Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) | ||
| Exam Code: | 200-201 Dumps | ||
| Vendor: | Cisco | Certification: | CyberOps Associate |
| Questions: | 476 Q&A's | Shared By: | aubree |
What specific type of analysis is assigning values to the scenario to see expected outcomes?
Refer to the exhibit.
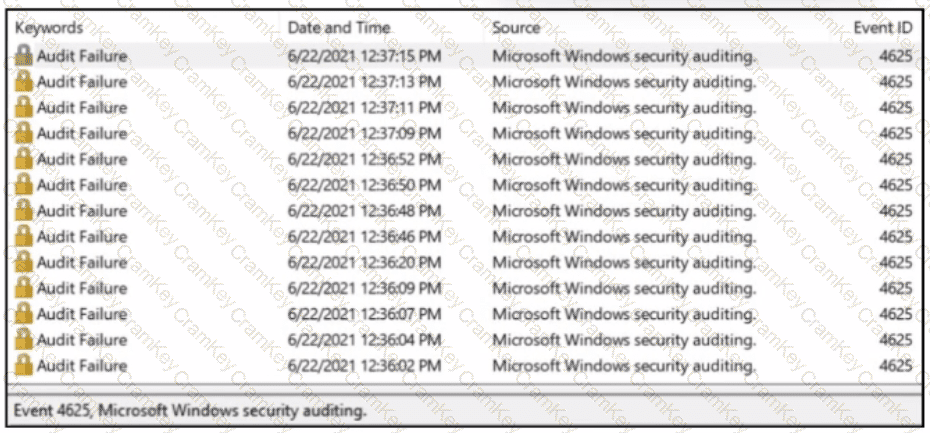
A SOC analyst received a message from SIEM about abnormal activity on the Windows server The analyst checked the Windows event log and saw numerous Audit Failures logs. What is occurring?
Which evasion method is being used when TLS is observed between two endpoints?
Syslog collecting software is installed on the server For the log containment, a disk with FAT type partition is used An engineer determined that log files are being corrupted when the 4 GB tile size is exceeded. Which action resolves the issue?