| Exam Name: | Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) | ||
| Exam Code: | 200-201 Dumps | ||
| Vendor: | Cisco | Certification: | CyberOps Associate |
| Questions: | 476 Q&A's | Shared By: | wilf |
What is the purpose of command and control for network-aware malware?
Which information must an organization use to understand the threats currently targeting the organization?
Refer to the exhibit.
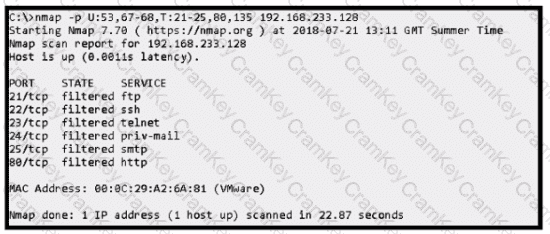
An attacker scanned the server using Nmap.
What did the attacker obtain from this scan?