| Exam Name: | Palo Alto Networks Certified Security Engineer (PCNSE) PAN-OS 11.0 | ||
| Exam Code: | PCNSE Dumps | ||
| Vendor: | Paloalto Networks | Certification: | Palo Alto Certifications and Accreditations |
| Questions: | 374 Q&A's | Shared By: | aysha |
Which translated port number should be used when configuring a NAT rule for a transparent proxy?
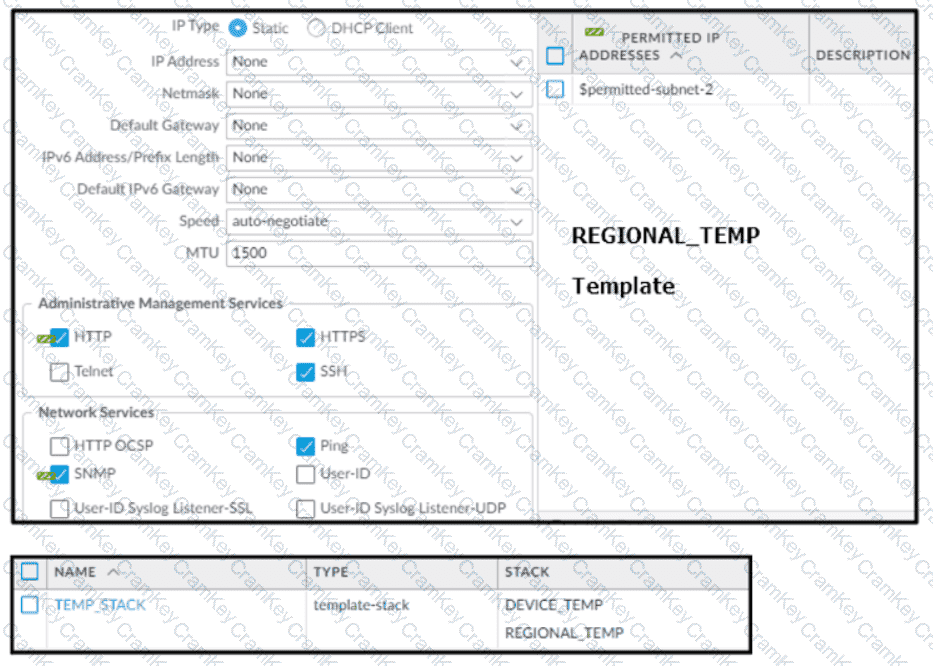
Based on the screenshots above, and with no configuration inside the Template Stack itself, what access will the device permit on its Management port?
A network administrator notices a false-positive state after enabling Security profiles. When the administrator checks the threat prevention logs, the related signature displays the following:
threat type: spyware category: dns-c2 threat ID: 1000011111
Which set of steps should the administrator take to configure an exception for this signature?
Which statement is correct given the following message from the PanGPA log on the GlobalProtect app?
Failed to connect to server at port:47 67