| Exam Name: | Certified Ethical Hacker Exam (CEHv13) | ||
| Exam Code: | 312-50v13 Dumps | ||
| Vendor: | ECCouncil | Certification: | CEH v13 |
| Questions: | 873 Q&A's | Shared By: | elis |
Which type of sniffing technique is generally referred as MiTM attack?
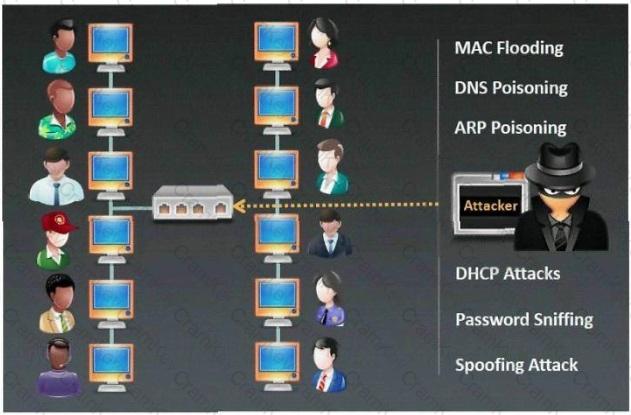
One customer’s malicious activity impacts other tenants. Which control would best prevent this?
A cybersecurity team identifies suspicious outbound network traffic. Investigation reveals malware utilizing the Background Intelligent Transfer Service (BITS) to evade firewall detection. Why would attackers use this service to conceal malicious activities?
A penetration tester is assessing a mobile application and discovers that the app is vulnerable to improper session management. The session tokens are not invalidated upon logout, allowing the tokens to be reused. What is the most effective way to exploit this vulnerability?