| Exam Name: | Architecting a Citrix Networking Solution | ||
| Exam Code: | 1Y0-440 Dumps | ||
| Vendor: | Citrix | Certification: | CCE-N |
| Questions: | 152 Q&A's | Shared By: | reeva |
Scenario: A Citrix Architect needs to design a hybrid Citrix Virtual App and Citrix Virtual Desktop environment which will include as well as resource locations in an on-premises datacenter and Microsoft Azure.
Organizational details and requirements are as follows:
Click the Exhibit button to view the conceptual environment architecture.
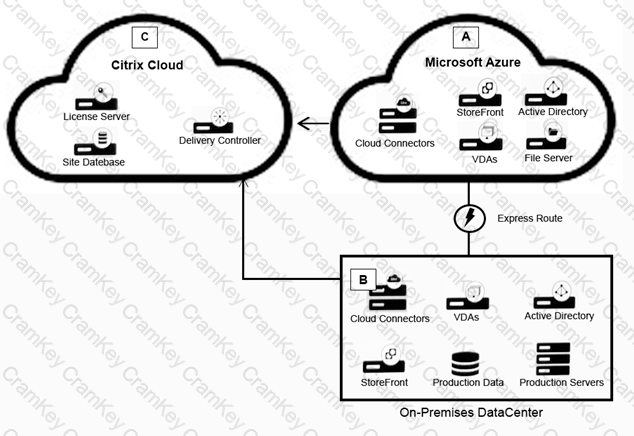
The architect should use___________ in Location A, and should use _______________ in Location B. (Choose the correct option to complete the sentence.)
Which format must a Citrix Architect utilize while importing the StyleBook in Citrix Application Delivery Management to compose the content of a StyleBook in the YAML editor?
Scenario: A Citrix Architect needs to assess an existing NetScaler gateway deployment. During the assessment, the architect collected key requirements for VPN users, as well as the current session profile settings that are applied to those users.
Click the Exhibit button to view the information collected by the architect.
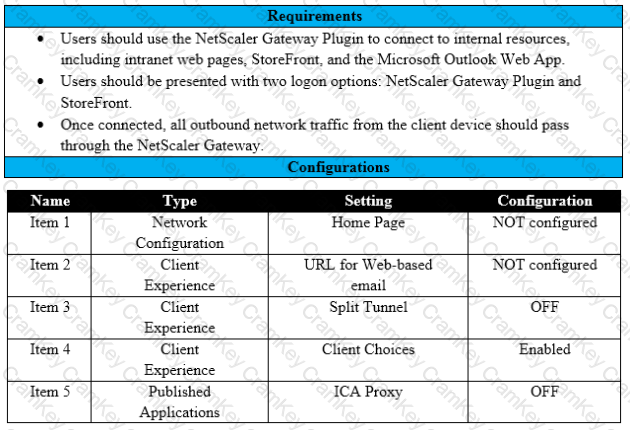
Which configuration should the architect change to meet all the stated requirements?
Scenario: A Citrix Architect has setup Citrix ADC MPX devices in high availability mode with version 12.0.53.13 nc. These are placed behind a Cisco ASA 5505 firewall. The Cisco ASA firewall is configured to block traffic using access control lists. The network address translation (NAT) is also performed on the firewall. The following requirements were captured by the architect during the discussion held as part of the Citrix ADC security implementation project with the customer's security team: The Citrix ADC MPX device:
Which security feature should the architect implement to meet these requirements?