| Exam Name: | CompTIA SecurityX Certification Exam | ||
| Exam Code: | CAS-005 Dumps | ||
| Vendor: | CompTIA | Certification: | CompTIA CASP |
| Questions: | 326 Q&A's | Shared By: | ariya |
A security engineer wants to improve the security of an application as part of the development pipeline. The engineer reviews the following component of an internally developed web application that allows employees to manipulate documents from a number of internal servers:
response = requests.get(url)
Users can specify the document to be parsed by passing the document URL to the application as a parameter. Which of the following is the best solution?
A company wants to modify its process to comply with privacy requirements after an incident involving PII data in a development environment. In order to perform functionality tests, the QA team still needs to use valid data in the specified format. Which of the following best addresses the risk without impacting the development life cycle?
During a forensic review of a cybersecurity incident, a security engineer collected a portion of the payload used by an attacker on a comprised web server Given the following portion of the code:
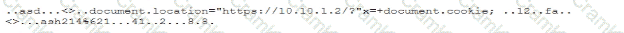
Which of the following best describes this incident?
An organization mat performs real-time financial processing is implementing a new backup solution Given the following business requirements?
* The backup solution must reduce the risk for potential backup compromise
* The backup solution must be resilient to a ransomware attack.
* The time to restore from backups is less important than the backup data integrity
* Multiple copies of production data must be maintained
Which of the following backup strategies best meets these requirement?