| Exam Name: | CompTIA SecurityX Certification Exam | ||
| Exam Code: | CAS-005 Dumps | ||
| Vendor: | CompTIA | Certification: | CompTIA CASP |
| Questions: | 326 Q&A's | Shared By: | ayub |
A threat hunter is identifying potentially malicious activity associated with an APT. When the threat hunter runs queries against the SIEM platform with a date range of 60 to 90 days ago, the involved account seems to be typically most active in the evenings. When the threat hunter reruns the same query with a date range of 5 to 30 days ago, the account appears to be most active in the early morning. Which of the following techniques is the threat hunter using to better understand the data?
Which of the following AI concerns is most adequately addressed by input sanitation?
The ISAC for the retail industry recently released a report regarding social engineering tactics in which small groups create distractions for employees while other malicious individuals install advanced card skimmers on the payment systems. The Chief Information Security Officer (CISO) thinks that security awareness training, technical control implementations, and governance already in place is adequate to protect from this threat. The board would like to test these controls. Which of the following should the CISO recommend?
A security analyst is troubleshooting the reason a specific user is having difficulty accessing company resources The analyst reviews the following information:
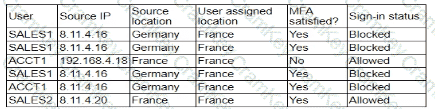
Which of the following is most likely the cause of the issue?