| Exam Name: | Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) | ||
| Exam Code: | 300-215 Dumps | ||
| Vendor: | Cisco | Certification: | CyberOps Professional |
| Questions: | 131 Q&A's | Shared By: | naia |
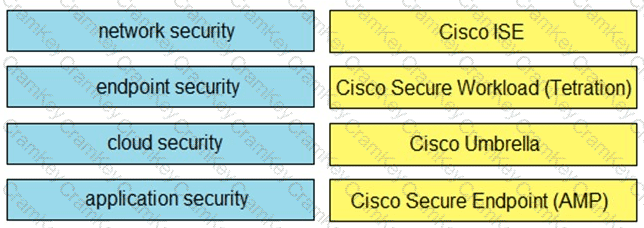
Drag and drop the capabilities on the left onto the Cisco security solutions on the right.
An engineer is analyzing a ticket for an unexpected server shutdown and discovers that the web-server ran out of useable memory and crashed.
Which data is needed for further investigation?
An organization experienced a ransomware attack that resulted in the successful infection of their workstations within their network. As part of the incident response process, the organization's cybersecurity team must prepare a comprehensive root cause analysis report. This report aims to identify the primary factor or factors responsible for the successful ransomware attack and to formulate effective strategies to prevent similar incidents in the future. In this context, what should the cybersecurity engineer emphasize in the root cause analysis report to demonstrate the underlying cause of the incident?
Refer to the exhibit.
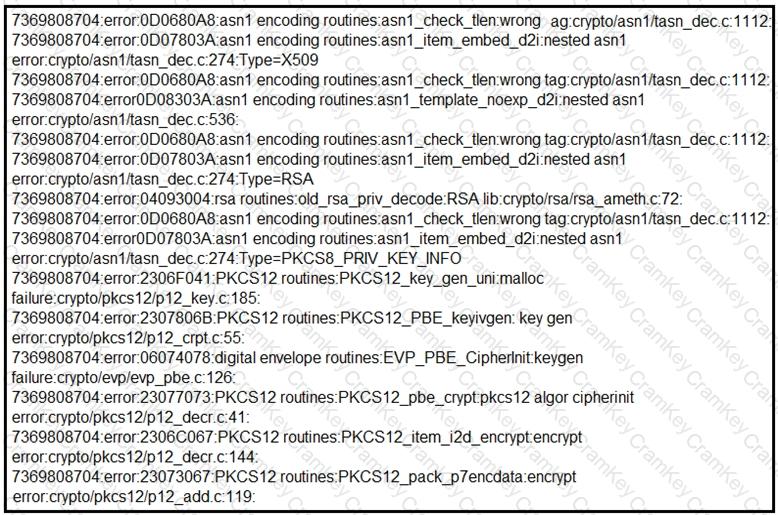
What should be determined from this Apache log?