| Exam Name: | Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) | ||
| Exam Code: | 300-215 Dumps | ||
| Vendor: | Cisco | Certification: | CyberOps Professional |
| Questions: | 131 Q&A's | Shared By: | hayley |
Refer to the exhibit.
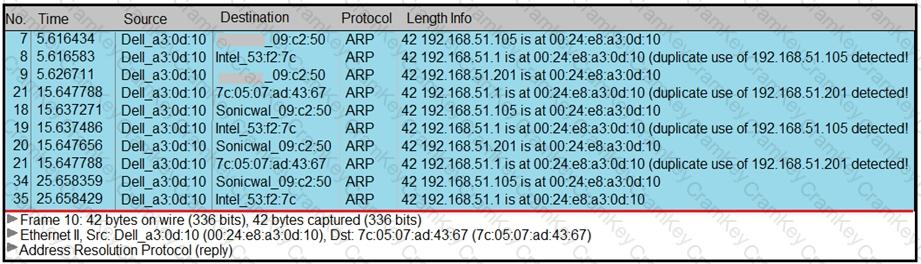
A security analyst notices unusual connections while monitoring traffic. What is the attack vector, and which action should be taken to prevent this type of event?
Refer to the exhibit.
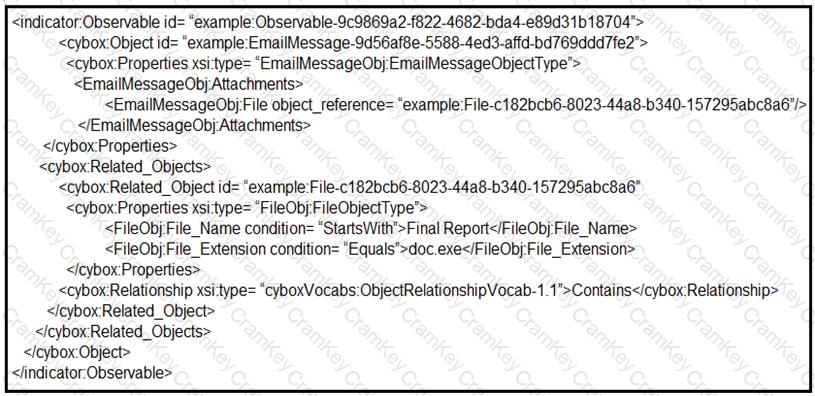
Which determination should be made by a security analyst?
Which information is provided about the object file by the “-h” option in the objdump line command objdump –b oasys –m vax –h fu.o?
What is the goal of an incident response plan?