| Exam Name: | Performing CyberOps Using Core Security Technologies (CBRCOR) | ||
| Exam Code: | 350-201 Dumps | ||
| Vendor: | Cisco | Certification: | CyberOps Professional |
| Questions: | 139 Q&A's | Shared By: | lucie |
An engineer wants to review the packet overviews of SNORT alerts. When printing the SNORT alerts, all the packet headers are included, and the file is too large to utilize. Which action is needed to correct this problem?
Refer to the exhibit.
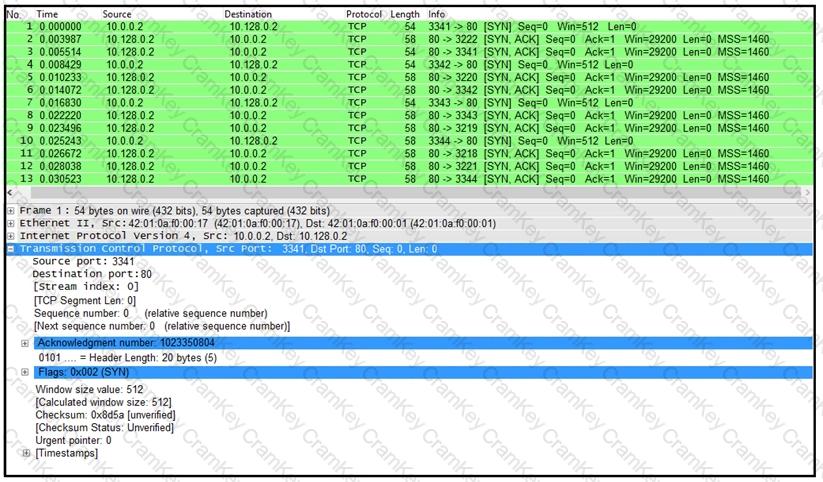
What is the threat in this Wireshark traffic capture?
A payroll administrator noticed unexpected changes within a piece of software and reported the incident to the incident response team. Which actions should be taken at this step in the incident response workflow?
An engineer implemented a SOAR workflow to detect and respond to incorrect login attempts and anomalous user behavior. Since the implementation, the security team has received dozens of false positive alerts and negative feedback from system administrators and privileged users. Several legitimate users were tagged as a threat and their accounts blocked, or credentials reset because of unexpected login times and incorrectly
typed credentials. How should the workflow be improved to resolve these issues?