Conducting Threat Hunting and Defending using Cisco Technologies for Cybersecurity 300-220 CBRTHD
Last Update Feb 5, 2026
Total Questions : 60
To help you prepare for the 300-220 Cisco exam, we are offering free 300-220 Cisco exam questions. All you need to do is sign up, provide your details, and prepare with the free 300-220 practice questions. Once you have done that, you will have access to the entire pool of Conducting Threat Hunting and Defending using Cisco Technologies for Cybersecurity 300-220 CBRTHD 300-220 test questions which will help you better prepare for the exam. Additionally, you can also find a range of Conducting Threat Hunting and Defending using Cisco Technologies for Cybersecurity 300-220 CBRTHD resources online to help you better understand the topics covered on the exam, such as Conducting Threat Hunting and Defending using Cisco Technologies for Cybersecurity 300-220 CBRTHD 300-220 video tutorials, blogs, study guides, and more. Additionally, you can also practice with realistic Cisco 300-220 exam simulations and get feedback on your progress. Finally, you can also share your progress with friends and family and get encouragement and support from them.
Refer to the exhibit.
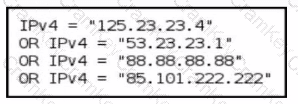
A threat-hunting team makes an EDR query to detect possible C2 outbound communication across all endpoints. Which level of the Pyramid of Pain is being used?
A threat hunter wants to detect fileless malware activity usingCisco Secure Endpoint. Which behavior would MOST strongly indicate fileless execution?
A mature SOC notices that several incidents over the past year involved attackers abusing legitimate administrative tools rather than deploying custom malware. Leadership asks the threat hunting team to improve detection coverage in a way that increases attacker cost rather than relying on easily replaceable indicators. Which detection strategy best aligns with this objective?
A SOC repeatedly discovers similar attacker behaviors during separate hunts, indicating recurring detection gaps. What process change MOST effectively prevents rediscovery of the same threats?