| Exam Name: | Conducting Threat Hunting and Defending using Cisco Technologies for Cybersecurity 300-220 CBRTHD | ||
| Exam Code: | 300-220 Dumps | ||
| Vendor: | Cisco | Certification: | Cisco Certified Specialist - Threat Hunting and Defending |
| Questions: | 60 Q&A's | Shared By: | rosalind |
Refer to the exhibit.
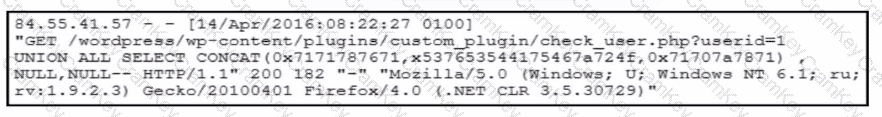
A forensic team must investigate how the company website was defaced. The team isolates the web server, clones the disk, and analyzes the logs. Which technique was used by the attacker initially to access the website?
The Security Operations Center team at a company detects a successful VPN connection from a country outside the known countries of operation. After the connection occurs, the team receives multiple triggers from the same source IP address about file access and modifications to the file server. The team concludes that this is a case of data exfiltration from an unknown adversary through a compromised user account. To find other potential actions taken by the adversary, which type of threat hunting should be used?
What is a limitation of automated dynamic malware analysis tools?