| Exam Name: | Conducting Threat Hunting and Defending using Cisco Technologies for Cybersecurity 300-220 CBRTHD | ||
| Exam Code: | 300-220 Dumps | ||
| Vendor: | Cisco | Certification: | Cisco Certified Specialist - Threat Hunting and Defending |
| Questions: | 60 Q&A's | Shared By: | aafiyah |
Refer to the exhibit.
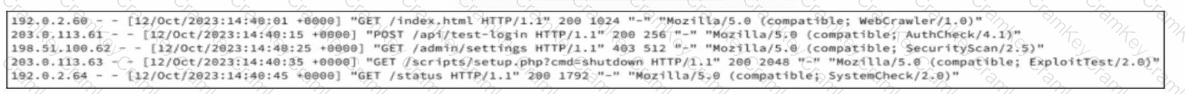
A company recently was breached and decided to improve their security posture going forward. A security assessment was ordered, specifically intended to test weak points exploited during the breach. A security analyst reviews server logs to identify activities related to the aforementioned security assessment. Which entry suggests a delivery method associated with authorized assessment?
A SOC team using Cisco security technologies wants to distinguishIndicators of Attack (IOAs)fromIndicators of Compromise (IOCs)during threat hunting. Which scenario BEST represents an IOA rather than an IOC?
After a multi-week threat hunting exercise, a security team confirms that an attacker gained access using valid credentials, moved laterally, and exfiltrated data without deploying malware. Senior leadership asks how the hunting program reduced organizational risk. Which outcome BEST demonstrates the value of threat hunting?
While investigating multiple incidents using Cisco telemetry, analysts notice that attackers consistently use valid credentials, avoid malware, and rely on remote management protocols. Why is this information valuable for attribution?