| Exam Name: | EC-Council Certified Security Analyst (ECSA) V10 | ||
| Exam Code: | 412-79v10 Dumps | ||
| Vendor: | ECCouncil | Certification: | ECSA |
| Questions: | 201 Q&A's | Shared By: | adnan |
Which of the following defines the details of services to be provided for the client’s organization and the list of services required for performing the test in the organization?
A firewall protects networked computers from intentional hostile intrusion that could compromise confidentiality or result in data corruption or denial of service. It examines all traffic routed between the two networks to see if it meets certain criteria. If it does, it is routed between the networks, otherwise it is stopped.
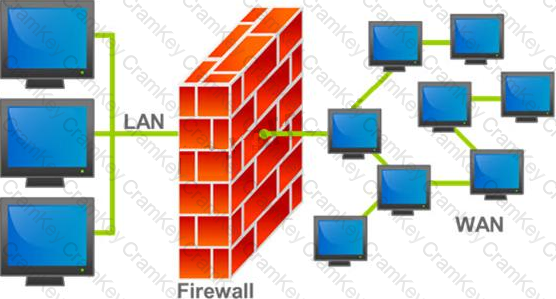
Why is an appliance-based firewall is more secure than those implemented on top of the commercial operating system (Software based)?
Identify the framework that comprises of five levels to guide agency assessment of their security programs and assist in prioritizing efforts for improvement: