Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)
Last Update Mar 2, 2026
Total Questions : 131
To help you prepare for the 300-215 Cisco exam, we are offering free 300-215 Cisco exam questions. All you need to do is sign up, provide your details, and prepare with the free 300-215 practice questions. Once you have done that, you will have access to the entire pool of Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) 300-215 test questions which will help you better prepare for the exam. Additionally, you can also find a range of Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) resources online to help you better understand the topics covered on the exam, such as Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) 300-215 video tutorials, blogs, study guides, and more. Additionally, you can also practice with realistic Cisco 300-215 exam simulations and get feedback on your progress. Finally, you can also share your progress with friends and family and get encouragement and support from them.
Refer to the exhibit.
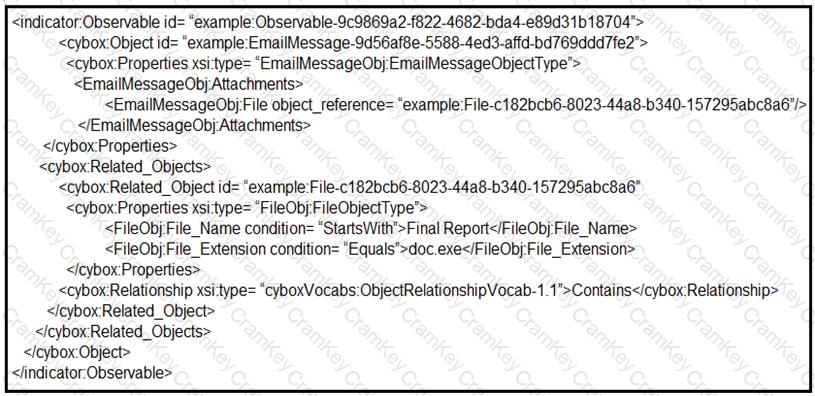
Which determination should be made by a security analyst?
An organization experienced a ransomware attack that resulted in the successful infection of their workstations within their network. As part of the incident response process, the organization's cybersecurity team must prepare a comprehensive root cause analysis report. This report aims to identify the primary factor or factors responsible for the successful ransomware attack and to formulate effective strategies to prevent similar incidents in the future. In this context, what should the cybersecurity engineer emphasize in the root cause analysis report to demonstrate the underlying cause of the incident?
Refer to the exhibit.
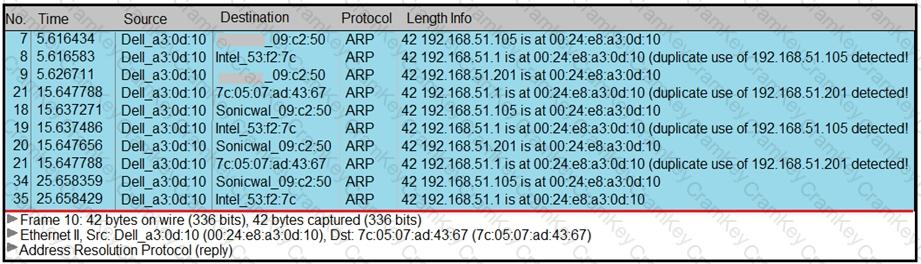
A security analyst notices unusual connections while monitoring traffic. What is the attack vector, and which action should be taken to prevent this type of event?