| Exam Name: | Netskope Certified Cloud Security Architect Exam | ||
| Exam Code: | NSK300 Dumps | ||
| Vendor: | Netskope | Certification: | NCCSA |
| Questions: | 68 Q&A's | Shared By: | ziggy |
You are asked to create a customized restricted administrator role in your Netskope tenant for a newly hired employee. Which two statements are correct in this scenario? (Choose two.)
Review the exhibit.
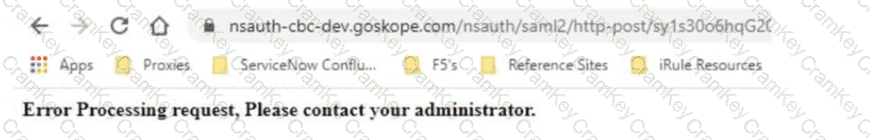
Netskope has been deployed using Cloud Explicit Proxy and PAC files. Authentication using Active Directory Federation Services (ADFS) has been configured for SAML Forward Proxy auth. When the users open their browser and try to go to a site, they receive the error shown in the exhibit.
What is a reason for this error?
Your company has a large number of medical forms that are allowed to exit the company when they are blank. If the forms contain sensitive data, the forms must not leave any company data centers, managed devices, or approved cloud environments. You want to create DLP rules for these forms.
Which first step should you take to protect these forms?
You have multiple networking clients running on an endpoint and client connectivity is a concern. You are configuring co-existence with a VPN solution in this scenario, what is recommended to prevent potential routing issues?