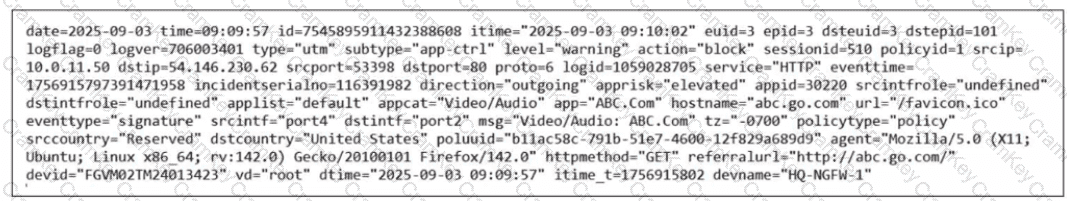
The exhibit shows a FortiGate UTM application control log with fields such as:
type="utm"
subtype="app-ctrl"
action="block"
policyid=1
appid=30220
appcat="Video/Audio"
service="HTTP"
apprisk="elevated"
This is a forward traffic security log, generated by Application Control applied to a firewall policy.
Why the correct answers are C and D
C. By filtering by policy universally unique identifier (UUID) and application name in the log entry
Correct.
FortiOS logs can be viewed and filtered in:
Log & Report → Forward Traffic
Administrators can filter logs using fields such as:
Policy ID / Policy UUID
Application name (app)
Application ID (appid)
The log entry clearly includes application-related fields, making filtering by policy and application a valid and documented way to view these logs.
D. In the Forward Traffic section
Correct.
The log is a UTM Application Control log for traffic passing through a firewall policy.
Such logs are displayed under:
Log & Report → Forward Traffic
This is the standard and correct location to view application control, web filter, IPS, and other security profile logs related to user traffic.
Why the other options are incorrect
A. By right clicking the implicit deny policy
Incorrect.
Implicit deny policies do not generate UTM forward traffic logs like the one shown.
Application control logs are generated only by explicit firewall policies with security profiles enabled.
B. Using the FortiGate CLI command diagnose log test
Incorrect.
diagnose log test is used to test log connectivity and log settings, not to view historical log entries.
It does not display traffic or UTM logs.