| Exam Name: | EC-Council Certified Security Analyst (ECSA) v10 : Penetration Testing | ||
| Exam Code: | ECSAv10 Dumps | ||
| Vendor: | ECCouncil | Certification: | ECSA |
| Questions: | 201 Q&A's | Shared By: | renzo |
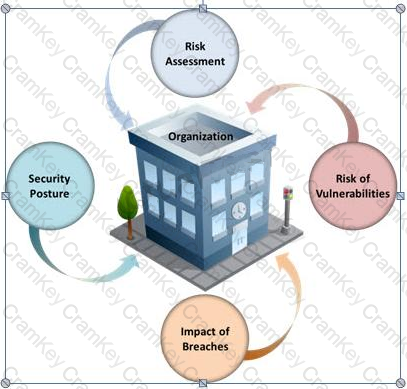
Many security and compliance projects begin with a simple idea: assess the organization's risk, vulnerabilities, and breaches. Implementing an IT security risk assessment is critical to the overall security posture of any organization.
An effective security risk assessment can prevent breaches and reduce the impact of realized breaches.
What is the formula to calculate risk?
John, the penetration testing manager in a pen testing firm, needs to prepare a pen testing pricing report for a client. Which of the following factors does he need to consider while preparing the pen testing pricing report?

Which of the following is NOT related to the Internal Security Assessment penetration testing strategy?