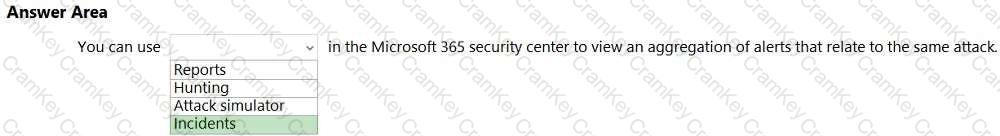
In Microsoft 365 Defender (Microsoft 365 security center), Incidents are designed to consolidate and correlate security signals so analysts can see the full scope of an attack. Microsoft’s documentation explains that an incident is “a collection of related alerts that, when viewed together, provide a richer context for the attack and its impact.” The service “automatically groups alerts that are likely to be associated with the same threat activity,” which allows security teams to investigate a single incident rather than many fragmented alerts. Microsoft further notes that incidents “aggregate alerts, affected assets (users, devices, mailboxes), evidences, and entities into one view,” helping analysts triage, investigate, and remediate more efficiently.
This is distinct from other areas in the portal: Reports provide trend and posture reporting; Hunting offers proactive, query-based threat hunting across raw data; and Attack simulator (in Defender for Office 365) is used to run training and awareness simulations (e.g., phishing), not to aggregate real alerts. Therefore, when you need to “view an aggregation of alerts that relate to the same attack” in the Microsoft 365 security center, the correct place is Incidents, which presents the correlated attack story and enables end-to-end response and remediation from a single, consolidated record.