| Exam Name: | FCSS Advanced Analytics 6.7 Architect | ||
| Exam Code: | FCSS_ADA_AR-6.7 Dumps | ||
| Vendor: | Fortinet | Certification: | Fortinet Certified Professional Security Operations |
| Questions: | 59 Q&A's | Shared By: | raymond |
Refer to the exhibit.
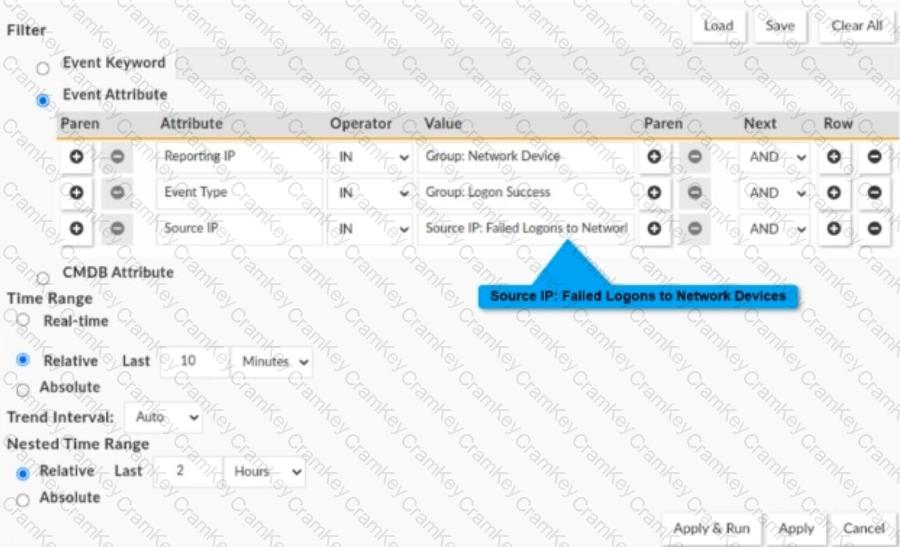
Consider a nested event query where both inner and outer queries are event queries.
Reporting IPis selected from the CMDB groupNetwork Device, Event Typeis selected from the CMDB groupLogon Success,andSource IPis selected from the reportFailed Logons to Network Devices.
An administrator is about to execute the nested query. The report time ranges must be set before execution. TheNested Time Rangewill be applied to which attributes?
Refer to the exhibit.

An administrator deploys a new collector for the first time, and notices that all the processes expect the phMonitor are down.
How can the administrator bring the processes up?
Refer to the exhibit.
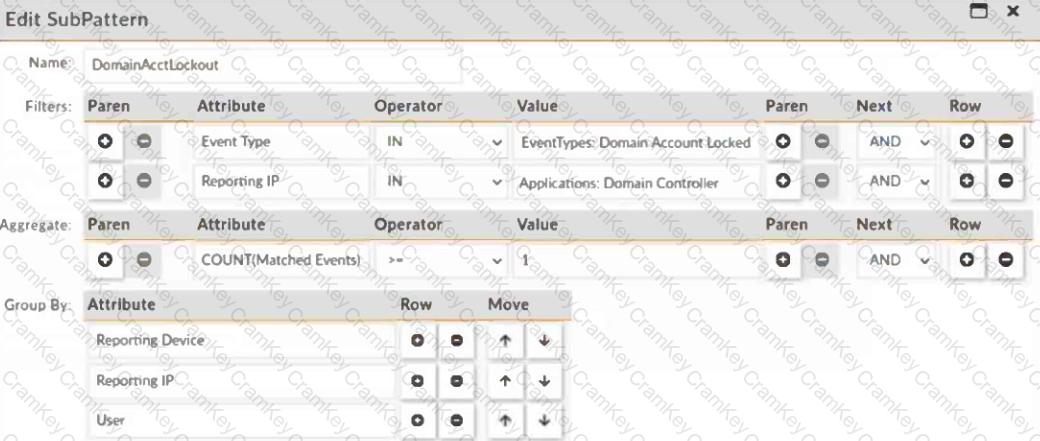
Which statement about the rule filters events shown in the exhibit is true?