ISACA Certified Cybersecurity Operations Analyst
Last Update Sep 16, 2025
Total Questions : 139
To help you prepare for the CCOA Isaca exam, we are offering free CCOA Isaca exam questions. All you need to do is sign up, provide your details, and prepare with the free CCOA practice questions. Once you have done that, you will have access to the entire pool of ISACA Certified Cybersecurity Operations Analyst CCOA test questions which will help you better prepare for the exam. Additionally, you can also find a range of ISACA Certified Cybersecurity Operations Analyst resources online to help you better understand the topics covered on the exam, such as ISACA Certified Cybersecurity Operations Analyst CCOA video tutorials, blogs, study guides, and more. Additionally, you can also practice with realistic Isaca CCOA exam simulations and get feedback on your progress. Finally, you can also share your progress with friends and family and get encouragement and support from them.
Question 1 and 2
You have been provided with authentication logs toinvestigate a potential incident. The file is titledwebserver-auth-logs.txt and located in theInvestigations folder on the Desktop.
Which IP address is performing a brute force attack?
What is the total number of successful authenticationsby the IP address performing the brute force attack?
Which ruleset can be applied in the
/home/administrator/hids/ruleset/rules directory?
Double-click each image to view it larger.
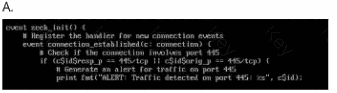
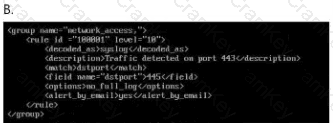
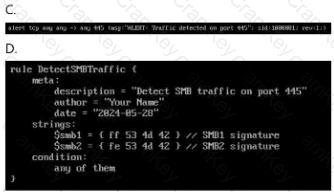
Which of the following has been defined when a disaster recovery plan (DRP) requires daily backups?
The user of the Accounting workstation reported thattheir calculator repeatedly opens without their input.
Perform a query of startup items for the agent.nameaccounting-pc in the SIEM for the last 24 hours. Identifythe file name that triggered RuleName SuspiciousPowerShell. Enter your response below. Your responsemust include the file extension.